AWAN 3883/4/5 Access Server Configuration and Management Manual
Configuring User and Port Access
AWAN 3883/4/5 Access Server Configuration and Management Manual—424242-001
7-7
Configuring User Access
Configuring User Access
To configure user access, you must perform the following steps:
1. Configure a user name and password for each user.
2. Enable the appropriate protocols for each user.
3. Configure user security for each user.
4. Synchronize the local and server user databases.
Use your User Configuration Worksheet while performing these steps.
Step 1: Creating the User Lists
To connect to the AWAN access server, a user must have a user name and a password.
You configure user names and passwords in the local and server user lists.When names
are added to the local and server user lists, users are prompted for a user name and
password before they are allowed a connection to the network.
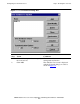
To create a user list, choose Users... from the Server Characteristics and Properties
menu. The User Database dialog box is displayed as shown in Figure 7-3
.
Note. You can set up authentication and authorization for remote access users.
Authentication is a function in which a user’s identity is verified. Authorization is the creation
of specific rights for a user once the user has been authenticated. For information about setting
up remote access security, refer to Section 13, Configuring Security for Remote Access Users.
Caution. Do not delete or assign a password to the GUEST user name. The GUEST user
name is required for the Autoconnect feature. It is provided by default and is defined without a
password. If the GUEST user name is deleted or is given a password, the Autoconnect feature
cannot be used.