NonStop S-Series Server Description Manual (G06.27+)
Interprocessor Communication
HP NonStop S-Series Server Description Manual—520331-004
9-10
Message Transfer Methods
Message Transfer Methods
Message System Protocol on page 9-6 shows that different kinds of transfers can use
different combinations of mechanisms. Sometimes the target processor of a message
can reverse roles to pull data from the originator of the message, and the request data
can be handled different ways depending on the length of the data.
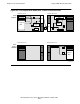
The upper part of Figure 9-5 tabulates the three basic phases that are used as a basis
for succeeding figures. Because the message system protocol requires a reply to each
request, there is always a reply upon which to piggy-back the acknowledgment to a
request, as shown in Figure 9-5. Therefore a separate acknowledge request phase is
never necessary. Frequently, also, the acknowledge reply can be piggy-backed on
some other message going in the same direction. However, a piggy-backed
acknowledge reply is not always possible, and so a separate acknowledge reply phase
is shown.
The request phase is implemented with three different mechanisms, one being chosen
depending on the combined length of the control and data information in the request.
The next three topics (Request With Short Request Data, Request With Medium
Request Data, and Request With Long Request Data) separately consider each of
these techniques of request processing. The final topic (Reply Data and Reply
Acknowledgement) considers the reply and reply acknowledge phases.
In different circumstances, either the request phase or the reply phase can use one of
two basis transfer methods—pre-push transfer or post-pull transfer.
The lower part of Figure 9-5 illustrates the difference between pre-push and post-pull
transfer methods. That difference is based on the placement of the setup packet in a
message. In the pre-push case, data is pushed by the sending processor from the
source buffer to the destination buffer ahead of (“pre-”) the setup packet. In the post-
pull case, the sending processor first pushes the setup packet (1), then the data is
pulled (2) by the receiving processor from the source buffer into the destination buffer
after (“post-”) the setup packet has been received. The control packets precede data in
either case.
Wherever possible, the message system uses the pre-push method. Because the
setup packet incurs an interrupt in the receiving processor, it is more efficient to send
the data first and then interrupt the processor to notify it that data is waiting, rather than
to interrupt first and then send the data packet by packet. However, the pre-push
method can be used only for transfers that fit in a pre-push buffer (currently 1920
bytes).
Every processor has four pre-push buffers for each processor that could be sending
messages to it. Therefore, in a 16-processor system, 15 processors could send
messages to any other, and there would be 15 times 4, or 60, pre-push buffers in each
processor.