TMF Application Programmer's Guide (G06.24+)
Designing Single-Threaded Processes
HP NonStop TMF Application Programmer’s Guide—522419-004
2-8
Checkpointing Strategy
backup requester. Data blocks are usually file buffers that are not checkpointed as
part of the stack and they can be from any location within the user data area (but
not an extended data area).
Instead of CHECKPOINT, there are three other checkpointing procedures that you will
sometimes need to use:
•
You use the CHECKPOINTMANY procedure when you need to checkpoint more
than 13 items from the user data area.
•
You use the CHECKPOINTX procedure when you need to checkpoint items from
an extended data area (up to five items).
•
You use the CHECKPOINTMANYX procedure when you need to checkpoint more
than five items from an extended data area.
Note that one of the pieces of information that must be in the data stack or one of the
data blocks is the tag value returned by BEGINTRANSACTION. In the event of a
primary-to-backup switch, the backup process might need that value to issue a
RESUMETRANSACTION call.
Whenever the primary process issues a CHECKPOINT call, the backup process must
issue a call to the CHECKMONITOR system procedure. This is often done in the form
of a loop in which a single CHECKMONITOR call is issued repeatedly until a primary-
to-backup switch occurs; when a switch occurs, control falls through the loop to the
takeover code.
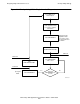
Figure 2-1 illustrates the proper placement of CHECKPOINT calls within the
transaction processing loop of a single-threaded primary TMF requester process.