TMF Introduction (G06.26+)
Transaction Protection and Database Recovery
HP NonStop TMF Introduction—522414-002
3-15
File Recovery
File recovery works by first restoring the data to the state of the last online dump of
data files. Then, TMF applies audit information, using both audit dumps and the
current audit-trail files. By applying audit information, file recovery can recover files to
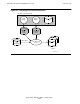
a time very close to when the failure occurred. This is a typical time-line for file
recovery:
Using this time-line, file recovery would involve these steps:
1. A failure has occurred, and a system operator initiates file recovery.
2. The file recovery process first restores the audited files from online dumps to the
state they were in when the dump was made: to the time of T1.
3. TMF restores the audit-trail files from audit dumps on tape made after the online
dump. TMF restores the audit dumps to restore-audit volumes and applies
changes from these audit-trail files to the database. Applying changes from Audit
Dump #1 restores the data to the time of T2; applying the changes from Audit
Dump #2 restores the data to the time of T3.
4. The file recovery process reads the current audit trail and applies the changes
recorded there, including removing the effects of any incomplete transactions. This
restores the data to the time of T4, when the failure occurred.
The file recovery process generates event messages while it runs, allowing you to
monitor the process. When file recovery is complete, the recovered files can be
opened.
File recovery requires a longer history of audit dumps than volume recovery. It needs
audit dumps for all audit-trail files written since the last online dump of a database file.
File recovery allows files to be recovered optionally to different volumes, subvolumes,
and file IDs than the ones on which they were dumped. The new (target) files,
however, must be located on the same node (system) and the same instance of TMF
as the old (source) files.
File recovery—with appropriate online dumps of database files, audit-trail dumps, and
sufficient disk space for its operations—completely protects the database files.
T1 T2 T3
T4
Online Dump
of Data Files
Failure
Time
Automatic Audit
Dump #1
Automatic Audit
Dump #2
Current Audit
Trail Files
VST057.vsd