TS/MP Pathsend and Server Programming Manual (G06.24+, H06.03+)
NonStop TS/MP Pathsend and Server Programming Manual–132500
2-1
2
Designing Your Application
To develop a functioning Pathway application, you must identify the individual
transactions in your business operations, design and build the application database, and
design and code requester programs and server programs. This section describes the
design of transactions and databases for Pathway applications and the design of
requester and server programs.
To explain these application design tasks, this section uses as an example an application
that processes sales orders for a distributorship. The example shows how the Pathway
environment can be used to create an OLTP application that supports the
distributorship’s order-processing operations.
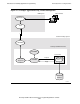
The distributorship in the example has three offices linked by telecommunications:
•
\CORP is a network node at corporate headquarters where the purchasing, accounts
receivable, and accounts payable functions are managed.
•
\WHS is a network node in a warehouse where the inventory, shipping, and
receiving functions are performed.
•
\REG is a network node in a sales office that is responsible for processing all
customer orders in a particular geographic region. Order-processing functions
consist of entering orders as input and maintaining records of each order. To perform
these two functions, the order processing group:
•
Checks with inventory control to determine if items to be ordered are in stock
•
Sends inventory control shipping and ordered-items information about each
order
•
Gets customer credit information from accounts receivable
•
Sends billing information to accounts receivable
•
Answers customer inquiries about order status
•
Records complete information about each order in the database
Designing Transactions
The first step in developing a Pathway application is to identify and define the
transactions that your application will process. To do this, you isolate the business tasks
you plan to automate, analyze the flow of information within those tasks, list the
transactions that result from the analysis, and then identify the various components of
the transactions. After these tasks are performed, you protect each transaction, and
therefore the integrity and consistency of the database, with the Transaction
Management Facility (TMF) subsystem.