HP ProCurve Threat Management Solution Design Guide 2009-04
4-16
Design
Follow an Iterative Design Process
Follow an Iterative Design Process
The design steps outlined in this section will take you through the initial setup and continuing
management of your network’s threat management functions. The steps are based on the
security management life cycle, which you should use as a general template for planning your
solution. You may want to think of the steps as “design and operation” steps, because you will
use them to adjust your solution design in response to the operational realities of your network.
This section explains which tasks you must perform. The HP ProCurve Threat Management
Solution Implementation Guide provides details on how to perform those tasks.
Step 1: Establish the Policy
The instructions for step 1 are divided into two sections:
■ First time through the process
■ Second and subsequent times through the process
First Time Through the Process
The NIM policies you create should be derived from your general network security policy. This
network security policy provides a guide for all security activities on your network, and as a
written document, it provides a solid basis for compliance with legal and regulatory require-
ments. Before creating actual NIM policies, you may want to conduct a thorough network
survey to identify the threats and vulnerabilities on your network. This survey should help you
determine what needs to be protected and which regulatory requirements you need to meet.
Collect Events. Because NIM policies define the response for specific threats, you should
start by listing the threats that could potentially plague your network. The first step in listing
threats is to establish what is normal on your network. ProCurve recommends that you
establish a baseline by setting up NIM and letting it collect information. You should let NIM
collect data at least one full day. Depending on your network, you may want to let it collect
data for several days or a week so that it can factor in both weekend and weekday activity. You
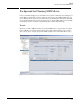
can view the NBAD Analysis Status area in the Network Immunity Manager Dashboard to see
whether NIM has completed the baseline for specific threats. (See Figure 4-10.)
Figure 4-10. NBAD Analyzer Status
You should then probably allow yourself several days of observing events, perhaps with
multiple cycles through the security management life cycle, to get a good feel for the threat
activity on your network.