HP ProCurve Threat Management Solution Implementation Guide 2009-05
3-40
HP ProCurve Network Immunity Manager with a Third-Party IDS/IPS
Step 2: Detect Threats
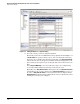
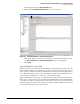
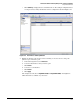
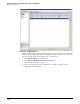
Figure 3-39. Editing the Actions in a Signature Policy
iv. Select the actions you want to assign that signature.
The default action for the 3002 TCP SYN Port sweep signature shown in Figure 3-39
is
Produce Alert
. Accept that action because it creates an entry in the sensor’s log.
To stop the detected malicious traffic from propagating, select Deny Packet Inline,
which causes the sensor to drop packets from the attacker that triggered the event.
(You would select this option if you are using the Cisco 4200 Series Sensor as an
IPS.)
Select Request SNMP Trap so the sensor will send a trap to the configured trap
receiver (the PCM+ management station) to notify it of the event.
Optionally, select Deny Attacker Inline. Although it seems as if Deny Attacker Inline
is redundant because you have already selected Deny Packet Inline, it is easy to see
the effect of Deny Attacker Inline because blocked attackers are displayed in the
Denied Attackers monitoring window. This makes it easier to verify that the Sensor
is taking the action that you configured.