HP ProCurve Threat Management Solution Implementation Guide 2009-05
3-44
HP ProCurve Network Immunity Manager with a Third-Party IDS/IPS
Step 2: Detect Threats
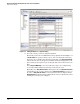
e. In the right pane, click Add. The Add Event Action Override window is displayed.
Figure 3-43. Overriding Event Action Defaults
f. For Risk Rating, select LOWRISK.
g. Select the check box in the Assigned column of the Deny Packet Inline (inline) action.
Make sure the corresponding Enabled check box is selected.
h. Click OK. The Deny Packet Inline action will now be triggered by events with a risk rating
of Low, such as the TCP Syn Port Sweep. You can disable the override at any time by
returning to the Event Action Overrides tab and deleting the override.
i. When you have finished editing and adding overrides, click Apply in the Event Action
Overrides window.
7. Configure exclusions for anomaly detection.
The sensor’s anomaly detection algorithms monitor your network traffic for patterns that
might be caused by viruses or other malware and do not rely on signatures for detection.
You might want to configure the Cisco 4200 Series Sensor to ignore traffic from devices
such as routers and management stations. Anomaly detection is sensitive to devices that
scan network ports, and could regard as malicious activity the legitimate attempts of
routers and management stations to probe or connect to large numbers of ports. You can
avoid false detection of such devices by instructing the sensor to ignore them in its anomaly
detection.
a. If necessary, click Anomaly Detections in the navigation bar to expand the list of
anomaly detection policies.
b. Select a policy.