HP ProCurve Threat Management Solution Implementation Guide 2009-05
3-45
HP ProCurve Network Immunity Manager with a Third-Party IDS/IPS
Step 2: Detect Threats
c. In the right pane, click the Operation Settings tab.
d. Make sure the Enable Ignored IP Addresses check box is selected.
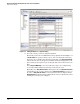
Figure 3-44. Excluding IP Addresses from Anomaly Detection
e. Enter the IP addresses of the devices you want to exclude from anomaly detection in
the Source IP Addresses and Destination IP Addresses boxes, as appropriate.
f. Click Apply.
Optional Subtask: Set Up an IPS
When the Cisco 4200 Series Sensor is used as an IPS, it operates in inline mode in the network.
Traffic flows through the sensor until it detects a virus or other threat; then it takes whatever
action you have configured, typically blocking traffic from the attacker and sending a notifica-
tion to NIM. In this way, the sensor can prevent malicious traffic from reaching critical areas
of your network, and NIM can act on the source of the malicious traffic.
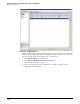
Figure 3-45 illustrates the IPS setup on a sample network. In this network, the IPS is placed
inline to protect the servers in a data center from attacks. Ordinarily the sensor allows all traffic
to pass from one segment of the network to the other. If the sensor detects an attack, it blocks
traffic from the attacker and it sends an alert to the management station. NIM can then respond
to the attack by shutting down the attacker’s port.