HP ProCurve Threat Management Solution Implementation Guide 2009-05
3-69
HP ProCurve Network Immunity Manager with a Third-Party IDS/IPS
Step 2: Detect Threats
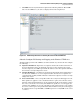
5. Click Next and enter any information required in the following windows. When PCM+
discovers the UTM device, the device is displayed in the left navigation bar.
Figure 3-69. PCM+ Management Interface Showing Discovered FortiGate UTM Device
Subtask: Configure IPS Settings and Logging on the Fortinet UTM Device
The IPS settings govern how the UTM detects malicious traffic on your network. You configure
the following:
■ Signature Definitions—Signatures are templates that describe malicious behavior on
the network (viruses and so on) and define responses to those behaviors. If a packet
matches a signature, the UTM responds with the defined action. The signature definition
also includes a severity rating for the attack.
■ Anomaly Definitions—Anomalies are departures from normal behavior. Anomaly detec-
tion allows the UTM device to detect suspicious traffic when there is no signature for
comparison. The anomaly definition includes a behavior description, as well as a severity
rating for the attack.
■ Protection Profiles—Protection profiles define the severity levels that trigger an event.
These profiles are applied to source-destination interface pairs, and events detected by
signature and anomaly definitions are checked against the profile for the interfaces where
the event occurs. If the event severity is included in the profile, the event is logged. For
example, if the UTM detects an event of medium severity and the interface pair on which
the event occurs has a protection profile that includes medium severity, the event is logged.
If communication is set up with PCM+, an SNMP trap is sent to notify PCM+ of the event’s
occurrence.