HP ProCurve Threat Management Solution Implementation Guide 2009-05
3-72
HP ProCurve Network Immunity Manager with a Third-Party IDS/IPS
Step 2: Detect Threats
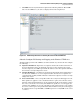
Figure 3-73. Edit Protection Profiles
d. Expand the IPS section to display these settings.
e. For IPS Signature and IPS Anomaly, select which levels of attack cause an event to be
logged.
If you want the UTM device to be sensitive to all potential threats, select the Low or
Information check boxes as well as the more severe settings. If you want the UTM device
to be relatively insensitive (that is, to register only the more severe attacks), select
only the Critical and High check boxes.
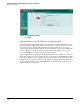
In Figure 3-74, all the check boxes for both signatures and anomalies are selected. The
Strict profile has been configured to trigger an event if anything at all occurs. This
setting makes it easier to test the UTM device’s interaction with PCM+/NIM (which
you will see later in the IPS and IDS descriptions).
In practice, you might not want even a strict profile to be so sensitive; configure the
settings that make sense for the activity on your network.
Figure 3-74. Configure the UTM Device’s Sensitivity to Events