HP ProCurve Threat Management Solution Implementation Guide 2009-05
3-76
HP ProCurve Network Immunity Manager with a Third-Party IDS/IPS
Step 2: Detect Threats
d. Click the editing icon for the policy row that you selected. The Edit Policy window is
displayed.
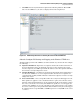
e. Select the Protection Profile check box to enable a profile, and then select a profile from
the drop-down list to the right.
Figure 3-79. Enabling a Protection Profile in a Firewall Policy
f. Click OK.
3. Optionally, test the IPS setup to verify that it is functioning properly.
a. Generate events. You can use port-scanning software, such as NMAP (which is
available at www.insecure.org), to probe the ports on your network in such a way that
the UTM device detects it as malicious traffic.
Alternatively, you can use the ping method. In the examples above on setting up IPS,
the UTM device was configured to detect the Echo.Reply signature as an attack. This
allows an attack event to be generated just by pinging a host on the other side of the
UTM device.
b. Check the UTM device for events. You can see the events in two different places:
– For a quick indication of event activity, you can view the Attack Log panel on the
System Status window. The IPS line under Attack Log shows the number of IPS
events logged. You can update the report by refreshing the window. (In the
navigation bar, click Status under the System tab.) If you want to see details of the
events, click Details at the end of the IPS line.