HP ProCurve Threat Management Solution Implementation Guide 2009-05
3-77
HP ProCurve Network Immunity Manager with a Third-Party IDS/IPS
Step 2: Detect Threats
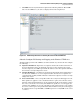
Figure 3-80. Attack Log Summary on the System Status Window
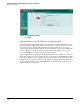
– Alternatively, you can check the UTM device’s log. In the navigation bar, click the
Log&Report tab; click Log Access; click the Memory tab; and in the Log Type list at
the top of the report, select Attack Log. The detailed log of attacks is displayed.
Figure 3-81. Attack Log