HP ProCurve Threat Management Solution Implementation Guide 2009-05
3-78
HP ProCurve Network Immunity Manager with a Third-Party IDS/IPS
Step 2: Detect Threats
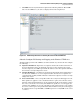
c. Verify that PCM+ receives the events. The event log in PCM+ shows events from the
sensor that are forwarded to PCM+/NIM as SNMP traps. To see an event in the PCM+
Event window, complete the following steps:
i. In the left navigation tree, click a group or device.
ii. Click the Events tab in the right pane.
Your event will be listed in the log, but given the number of events that PCM+ logs,
knowing the time the event occurred on the UTM device (and having the UTM
device and PCM+ synchronized) will help you to locate it. In addition, the name
of the signature or anomaly reported in the UTM device’s event log is included in
the SNMP trap. You can find the event quickly by entering that name in the
Description field in the Filters section of the PCM+ Event window.
Figure 3-82. PCM+ Event Window with Events from the FortiGate UTM Device
Once you are confident that the events from the UTM device are being reported to
PCM+, you can set up a non-ProCurve Security Devices alert in NIM’s Policy Manager
to capture the event, and you can set up a policy to respond to the event with an
appropriate action.
Optional Subtask: Set Up an IDS
When the Fortinet FortiGate UTM is used as an IDS, it operates in off-line mode in the network.
Using the port mirroring function of ProCurve switches, traffic from a port of interest (typically
a port on which you expect or have seen suspected attack activity) is copied to the IDS. The
IDS analyzes the traffic, and if it detects a virus or other threat, it alerts PCM+/NIM. PCM+
receives the alert and hands it off to NIM for appropriate action, such as shutting down the
attacker’s port.