HP ProCurve Threat Management Solution Implementation Guide 2009-05
3-81
HP ProCurve Network Immunity Manager with a Third-Party IDS/IPS
Step 2: Detect Threats
Check for successful SNMP communication with PCM+ by using the Manual Discovery
Wizard in PCM+ (Tools > Manual Discovery Wizard) to discover the UTM device.
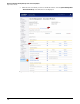
6. In the left navigation bar, click the Firewall tab and then click Policy. Make sure that no
policy is configured for the interface pairs on which the sniffer port resides (as either a
source or destination). If a policy is configured, disable it by clearing the check box on the
left of the policy entry for that interface pair.
7. Configure the sniffer port on the UTM device. You will use the CLI to enter these
configuration commands. You can enter the CLI commands through a console session, a
Telnet session, or the Web browser interface’s CLI panel.
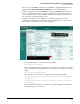
Figure 3-86. Accessing the CLI Through the Web Browser Interface
a. For the sniffer interface, enter the following commands:
set arpforward disable
This command prevents the looping that would otherwise occur when the two UTM
device ports (management and sniffer) are connected to the same switch on the same
VLAN.
set ips-sniffer-mode enable
This command causes the device to examine traffic in IDS mode (off-line).
set ips-sniff-signature severity [severity [severity [severity
[severity]]]]
set ips-sniff-anomaly severity [severity [severity [severity
[severity]]]]
These commands determine the severity level of attack that will trigger the UTM device
to log an intrusion protection event.