HP ProCurve Threat Management Solution Implementation Guide 2009-05
3-101
HP ProCurve Network Immunity Manager with a Third-Party IDS/IPS
Step 2: Detect Threats
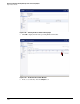
7. The Edit Rule window is displayed. In the Action line, click Allow.
Figure 3-108. The Edit Firewall Rule Window
8. Click OK.
At this point your UTM device functions somewhat like an Ethernet cable, allowing traffic to
pass in both directions. To test the setup, confirm that packets can pass through the device as
follows:
1. From a host on the X0 side of the UTM device, ping a host or device on the X1 side.
2. From a host on the X1 side of the UTM device, ping a host or device on the X0 side.
If both pings are successful, the initial setup is complete.
Subtask: Set Intrusion Protection Parameters and Logging
Setting up intrusion protection involves:
■ Installing the license keyfile
■ Installing the signatures
■ Configuring intrusion protection settings
■ Setting up logging
■ Testing
Install the License Keyfile. The intrusion prevention functions of the UTM device require
that the license key string be installed. You downloaded the license key string from the
SonicWALL site during the initial setup of the device. To install the license key string, complete
the following steps:
1. Access the device’s Web browser interface.
2. In the left navigation bar, click System > Licenses.
3. On your management station, use a text editor such as Notepad to open the license key file.
4. Copy the text of the license key and paste it into the Or enter keyset box in the GUI.