HP ProCurve Threat Management Solution Implementation Guide 2009-05
C-4
Configure VPNs Using the HP ProCurve Threat Management Services zl Module
Configure a Site-to-Site IPsec VPN
Configure a Site-to-Site IPsec VPN
This section explains how to configure a site-to-site IPsec VPN between two TMS zl Modules.
For this example, the modules authenticate each other with digital certificates, and instructions
are included for installing these certificates.
You must complete these tasks on each module:
1. Create named objects.
See “Create Named Objects for the VPN” on page C-4. (Using named objects is best practice;
however, you can specify IP addresses manually.)
2. Create an IKE policy.
See “Create an IKE Policy” on page C-6.
3. Install the correct certificates on the TMS zl Module.
See “Install Certificates for IKE” on page C-10.
4. Create an IPsec proposal.
See “Create an IPsec Proposal for a Site-to-Site IPsec VPN” on page C-17.
5. Create an IPsec policy.
See “Create an IPsec Policy for a Site-to-Site VPN That Uses IKE” on page C-19.
6. Create the necessary firewall access policies.
See “Create Access Policies for an IPsec Site-to-Site VPN with IKE” on page C-23.
7. Create a static route, if necessary.
See “Verify Routes” on page C-27.
Create Named Objects for the VPN
You can specify named objects in the IPsec policy traffic selector and in corresponding firewall
access policies. Note that an IPsec policy requires single-entry address objects, so you should
create objects of this type.
For this VPN configuration, create four address objects:
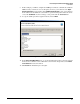
1. Click Firewall > Access Policies and then click the Addresses tab.
2. Click Add an Address.
3. Create an object for the local VPN gateway address:
a. For Name, type a name that is meaningful to you. For this example, type LocalGateway.
You can use only letters, numbers, and the underscore character (_) in this field.
b. For Type , select IP.