HP ProCurve Threat Management Solution Implementation Guide 2009-05
2-28
HP ProCurve Network Immunity Manager Standalone Solution
Step 3: Respond to Threats
Step 3: Respond to Threats
This section discusses the activities you might engage to define actions for NIM events. These
activities follow the “Respond to threats” phase of the security management life cycle (see
Figure 2-1 on page 2-3), and they match the design steps discussed in Chapter 4: “Design” in
the HP ProCurve Threat Management Solution Design Guide. That is, if you are following the
steps in the design guide, this section will guide you through the activities that accomplish the
respond to threats step.
First Time Through the Process
The first time through the process, you have two choices:
■ Skip this step
■ Ensure policy execution is disabled
Skip This Step
ProCurve recommends that you skip this step and go to “Step 4: Analyze Events” on page 2-44.
The first time through the process, you are just establishing the baseline level of threat activity
on your network, and you do not need to take any action against those threats. This allows you
to gain an overall familiarity with all the potential threats and activities on your network,
allowing you to take better-coordinated actions than if you start responding to threats from
the outset.
Task: Ensure Policy Execution Is Disabled
Alternatively, if you decide to set up actions and policies the first time you go through the
process, you should keep the default setting for policy execution: you should ensure that policy
execution is disabled. You will then be able to see which actions NIM would have taken in
response to threats, but those actions will not actually be enforced. This allows you to verify
that NIM detects threats and responds to them but defer actual execution of the responses
until you have a better understanding of threat activity on your network.
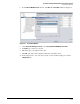
You can quickly determine whether or not this setting is enabled or disabled by looking at the
bottom right corner of any PCM+ window. In Figure 2-26, for example, you can see the words
“Policy configuration actions disabled.” The setting is disabled.