HP ProCurve Threat Management Solution Implementation Guide 2009-05
C-75
Configure VPNs Using the HP ProCurve Threat Management Services zl Module
Configure a Client-to-Site IPsec VPN for Macintosh IPSecuritas Clients
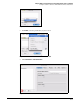
13. Click the Phase 1 tab and configure the following, which must match settings in the IKE
policy on the TMS zl Module:
a. For Lifetime, select Seconds, then type a value in the box. For this example, type 28800.
b. For DH Group, select one of the following:
– 768 (1) — DH group 1
– 1024 (2) — DH group 2
– 1536 (5) — DH group 5
For this example, select 768 (1).
c. For Encryption, select one of the following:
i. DES
ii. 3DES
iii. AES 128
iv. AES 192
v. AES 256
For this example, select 3DES.
d. For Authentication, select one of the following:
i. MD5
ii. SHA-1
For this example, select MD5.
e. For Exchange Mode, select Main or Aggressive. For this example, select Aggressive.
Figure C-91. IPSecuritas—Connections > Phase 1 Tab
14. Accept the remaining defaults and click the Phase 2 tab.
15. Configure the following settings, which must match settings in the TMS zl Module’s IPsec
proposal and IPsec policy:
a. For Lifetime, select Seconds and type a value in the box. For this example, type 28800.
b. For PFS Group, select one of the following:
– 768 (1) — DH group 1
– 1024 (2) — DH group 2
– 1536 (5) — DH group 5
For this example, select 1024 (2).