HP ProCurve Threat Management Solution Implementation Guide 2009-05
2-38
HP ProCurve Network Immunity Manager Standalone Solution
Step 3: Respond to Threats
10. Click the Sources tab to configure sources from which an alert must originate to trigger
the policy.
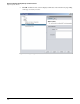
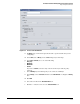
Figure 2-36. <PortAnomaly-Port shut> > Sources Window
11. Specify the source:
Note When specifying a source, be extremely careful. Keep in mind that the source is the device that
sends the sFlow data—not necessarily the device to which the offender is connected.
a. Any source—If you want the policy to act on alerts from any source, leave Any source
under Selected Groups.
b. Selected sources—If you want to the policy to act on alerts only from a specific group
of sources, complete one of the following:
i. Select a group from the Available Groups list.
Note When IDM is installed, you can use groups that are already configured for IDM locations.
ii. Click Add > to move the selected group to the Selected Groups list.