HP ProCurve Threat Management Solution Implementation Guide 2009-05
2-41
HP ProCurve Network Immunity Manager Standalone Solution
Step 3: Respond to Threats
17. Click the Actions tab.
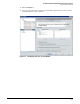
Figure 2-39. <PortAnomaly-Port shut> > Actions Window
18. In the Available Actions list, select the action that you want the policy to execute when the
configured alert is received. If the action you want is not in the Available Actions list, you
can create it as explained in “Task: Define an Action” on page 2-30.
19. Click the >> button to move the action to the Selected Actions list.
Note that you can specify multiple actions. If you have multiple actions, they are performed
in the order in which they are listed in the Selected Actions list. You can click Move Up and
Move Down to rearrange the order of the actions.
Note The action is applied as soon as the policy is executed. If you are running IDM (and have not
specifically disabled IDM-NIM integration), IDM will reapply this action to the user if the user
attempts to connect to another switch port or AP.
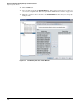
20. Select one of the following:
• Execute All—NIM performs all actions on all target devices in the specified order.
• Execute Until Success—NIM attempts actions in order on each target device until
an action succeeds, then moves on to the next target device.
• Act on Edge Ports Only—NIM attempts the actions on edge ports if the action is
port-oriented.
21. Optionally, select the Rollback Actions check box to set a rollback interval. The action is
undone at the end of the rollback interval. For instance, you could respond to an alert by
blocking the source port for five minutes and then unblocking the port.
22. Click Close or Apply to complete the policy definition. Clicking Apply completes the policy
definition; clicking Close completes the definition and closes the Policy Manager.