HP TMS zl Module Security Administrator's Guide
4-194
Configuring a VPN on the HP TMS zl Module
Configuring an IPsec Site-to-Site VPN with IKE
Create Access Policies for the TMS zl Modules in the IPsec
Site-to-Site VPN
Before you begin configuring firewall access policies, you need to examine
the zones on each of your TMS zl Modules. For each module, determine the
following:
■ Zone or zones on which the other module or modules reach this module—
This will be called the remote zone
■ Zone or zones for local endpoints allowed on the VPN. This might be the
Internal zone or another zone. If multiple zones are allowed to access the
VPN, you must create policies for each of these zones.
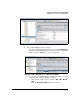
Figure 4-128 shows zones for an example IPsec site-to-site VPN.
Figure 4-128. Example IPsec Site-to-Site VPN (with Zones)
Table 4-20 lists the necessary access policies; the numbers in the Source and
Destination columns refer to the example figure above. (Note that all of these
policies are typically configured for the None user group. However, if local
users log in through the module, then the access policies with the local zone
as the source zone would need to be configured for their user groups.)
For access policies that permit the traffic sent over the tunnel, you should
consider setting the TCP MSS to a value lower than the typical MSS used in
your system—particularly, when IPsec fragmentation is disabled. Otherwise,
the addition of the IPsec and IP delivery headers might make the packets too
large to be transmitted. Table 4-24 suggests a conservative value for the TCP
MSS when the MTU is 1500. For more information on the TCP MSS, see
Chapter 6: “Configuring the TMS zl Module Firewall.”