HP TMS zl Module Security Administrator's Guide
4-220
Configuring a VPN on the HP TMS zl Module
Configuring an IPsec Site-to-Site VPN with IKE
The position determines the order in which the TMS zl Module processes
IPsec policies. The module processes the policy with the lowest value first
(for example, position 1 before position 2). The position matters most
when policies have overlapping traffic selectors. In this case, assign the
highest position (lowest value) to the IPsec policy with the most specific
traffic selector.
A default IPsec policy prevents all traffic from being encrypted by the VPN
engine; therefore, all IPsec policies that you configure must have a higher
priority than this default policy.
Next, you configure the VPN traffic selector, which determines which traffic
will use the VPN tunnel. For example, the selector might specify all IP traffic
between 192.168.2.0/24 (a local network) and 192.168.3.0/24 (a remote net-
work). For a policy with the Apply action, the selected traffic is the traffic that
is sent and received (and secured) on the IPsec SA.
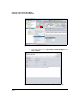
Refer to Figure 4-149 for help in configuring the next settings.
Figure 4-149. Example IPsec Site-to-Site VPN
8. For Traffic Selector, configure these settings:
a. For Protocol, specify the protocol for traffic allowed on the VPN:
– Any—Any IP protocol. Select this option when you want to allow
all traffic between local and remote endpoints.
– TCP or UDP—Select this option in conjunction with a remote port
to allow local traffic destined for specific services in the remote
network. Select this option in conjunction with a local port to
allow remote traffic destined for specific services in the local
network.
– ICMP—Select this option if you want to allow only ICMP traffic.