HP VPN Firewall Appliances NAT and ALG Configuration Guide
58
ALG process
The following example describes the FTP operation of an ALG-enabled device.
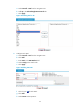
As shown in Figure 39, the host on the exter
nal network accesses the FTP server on the internal network
in passive mode through the ALG-enabled device.
Figure 39 Network diagram for ALG-enabled FTP application in passive mode
The communication process includes the following steps:
1. Establishing a control connection.
The host sends a TCP connection request to the server. If a TCP connection is established, the server
and the host enter the user authentication stage.
2. Authenticating the user.
The host sends the server an authentication request, which contains the FTP commands (user and
password) and the contents.
When the request passes through the ALG-enabled device, the commands in the payload of the
packet are resolved and used to check whether the protocol state transition is correctly proceeding.
If not, the request will be dropped. In this way, ALG protects the server against clients that send
packets with state errors or log in to the server with unauthorized user accounts.
An authentication request with the correct state is forwarded by the ALG-enabled device to the
server, which authenticates the host according to the information in the packet.
3. Establishing a data connection.
If the host passes the authentication, a data connection is established between it and the server. If
the host is accessing the server in passive mode, the server sends the host a PASV response that
uses its private network address and port number (IP1, Port1). When the response arrives at the
ALG-enabled device, the device resolves the packet and translates the server's private network
address and port number into the server's public network address and port number (IP2, Port2)
respectively. Then, the device uses the public network address and port number to establish a data
connection with the host.