Management and Configuration Guide (Includes ACM xl) 2005-12
ProCurve Secure Access 700wl Series Management and Configuration Guide 6-15
Configuring the Network
Note: You cannot enable redundancy (the check box will not be active) until a connection with
the peer Access Control Server has been established.
Step 4.
When you are ready to initiate the peer relationship and start the data synchronization process,
check the
Enable Redundancy check box on the Primary Access Control Server (and Save). You
only need to configure and enable redundancy on the primary Access Control Server to make
the relationship active.
Step 5. To ensure proper network synchronization, make sure the time and date on the preferred
primary Access Control Server and the secondary Access Control Server match by either
setting them both manually or setting them both to access an NTP server. See “Setting the Date
and Time” on page 6-41 for more information.
Note:
Once the redundant peer relationship is active, the configuration on the Secondary Access
Control Server is overwritten by the configuration of the Primary Access Control Server. Further, when
you disable the redundancy, the secondary Access Control Server is reset to factory defaults. If you care
about the configuration information of the second Access Control Server, it is recommended that you
back up the second Access Control Server before you initiate the peer relationship.
Once redundancy is operational, refreshing the browser window changes the Access Control Server
label at the upper right of the Header bar to indicate whether the Access Control Server is acting as a
primary or secondary Access Control Server.
When running the Administrative Interface on the Primary Access Control Server, the label in the
Header bar will show “Primary Access Control Server.”
When running the Administrative Interface on the secondary Access Control Server, the Header bar
label shows “Secondary Access Control Server,” and the word “secondary” appears in large letters in
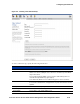
the center of the Header bar, as shown inFigure 6-7.
Figure 6-7. System Components List of a Secondary Access Control Server
The Secondary Access Control Server
A Secondary Access Control Server does not support a full set of configuration capabilities. Only
minimal network configuration and maintenance functions (such as software update, backup and
restore) are allowed. The Rights and VPN functions are not available at all from a Secondary Access