Secure Access Configuration Guide For Wireless Clients Part Two: Wireless Data Privacy and Monitored Logon 2003-03
Configuring Scenario 5: Wireless Data Privacy Logon using VPN
Authentication (L2TP/IPSec)
Scenario 5 consists of a wireless, Windows XP client authenticating via a VPN. The VPN used in
this example will be an L2TP/IPSec VPN. Since VPN authentication requires a RADIUS backend,
we will configure an ACS to authenticate VPN users against Internet Authentication Service
(IAS), Microsoft’s RADIUS implementation. The steps required are:
• On the ACS, enable L2TP and IPSec VPN support globally.
• On the ACS, configure Unauthenticated and Authenticated Access Policies for:
¾ L2TP/IPSec VPN support
¾ Real IP addresses inside the encrypted VPN tunnel
• On the ACS, define a RADIUS Authentication Service and associate it to the System
Authentication Policy.
• From the ACS, configure the ProCurve Access Control xl Module with the DHCP
Server IP Address to allow clients to use Real IP addresses for the inner VPN tunnel.
• On the AP 420, configure open authentication wireless parameters.
• On the wireless Windows XP client, configure the ProCurve VPN and Windows XP
VPN client software for L2TP/IPSec.
• Connect and verify authentication.
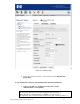
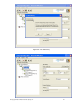
1) On the ACS, enable L2TP and IPSec support globally.
a. On the ACS, browse to VPN -> Wireless Data Privacy tab and click the
Enable IPSec and Enable L2TP+IPSec checkboxes. Select the radio
button to enable IPSec Shared Secret for IKE Authentication Method and
configure an IPSec shared secret. Leave all other configuration settings
default and save changes.
Figure 5.1 – Wireless Data Privacy
© Copyright 2005 Hewlett-Packard Company, LP. 23