Secure Access Configuration Guide For Wireless Clients Part Two: Wireless Data Privacy and Monitored Logon 2003-03
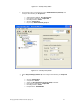
Figure 5.9 – Security Policy Editor
f. Click Security Policy and expand to select Authentication (Phase1) and
configure the following for Proposal 1:
¾ Authentication Method: Pre-Shared Key
¾ Encryp(tion) Alg(orithm): Triple DES
¾ Hash Alg(orithm): SHA-1
¾ SA Life: Unspecified
¾ Key Group: Diffe-Hellman group 2
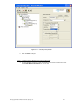
Figure 5.10 – Security Policy Editor
g. Select Key Exchange (Phase 2) and configure the following for Proposal
1:
¾ SA Life: Unspecified
¾ Compression: None
¾ Select the Encapsulation Protocol (ESP) checkbox
¾ Encryp(tion) Alg(orithm): Triple DES
¾ Hash Alg(orithm): SHA-1
¾ Encapsulation: TRANSPORT
© Copyright 2005 Hewlett-Packard Company, LP. 31