Secure Access Configuration Guide For Wireless Clients Part Two: Wireless Data Privacy and Monitored Logon 2003-03
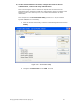
Figure 6.19 – Define Certificate
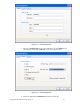
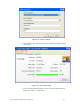
e. Verify wireless client authentication and IP addressing using the Proxim
Client Utility.
Figure 6.20 – Proxim Client Utility
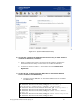
f. On the ACS Management interface, verify successful authentication by
browsing to Status -> Client Status.
© Copyright 2005 Hewlett-Packard Company, LP. 58