TMS zl Management and Configuration Guide ST.1.0.090213
7-170
Virtual Private Networks
Configure the VPN Client
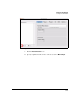
Key Exchange Mode Main or Aggressive, as configured in step 14e on page 7-163 Add IKE Policy—Step 2 of 3
Authentication
Method
Preshared Key
Preshared Key Same key as configured in step 17– on page 7-166
Diffie-Hellman (DH)
Group
Matches the setting configured in step 14b on page 7-163
Encryption Algorithm Matches the setting configured in step 14c on page 7-163
Authentication
Algorithm
Matches the setting configured in step 14d on page 7-163
SA Lifetime in
seconds
Matches the setting configured in step 14a on page 7-163
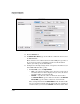
XAUTH Configuration Disable XAUTH Add IKE Policy—Step 3 of 3
IPsec proposal
Encapsulation Mode Tunnel Add IPsec Proposal
Protocol ESP
Encryption Algorithm
(if you selected ESP)
Matches the setting configured in step c on page 7-164
Authentication
Algorithm
Matches the setting configured in step d on page 7-164
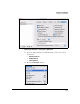
IPsec policy
Action Apply Add IPsec Policy—Step 1 of 4
Position Any but last
Protocol Any
Local Address Matches the setting configured in step b on page 7-163
Remote Address Matches the setting configured in step a on page 7-162
Proposal The IPsec proposal that you configured for the Macintosh clients
IKEv1 Policy The client-to-site IKE policy that you configured for the
Macintosh clients
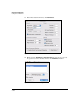
Add IPsec Policy—Step 2 of 4
Enable PFS (Perfect
Forward Secrecy) for
keys
Matches the setting configured in step b on page 7-164
Diffie-Hellman (DH)
Group (if you enabled
PFS)
Matches the setting configured in step b on page 7-164
SA Lifetime in
Seconds
Matches the setting configured in step a on page 7-164
SA Lifetime in
Kilobytes
Matches the setting configured in step a on page 7-164
Parameter Valid Settings Configuration Window