TMS zl Management and Configuration Guide ST.1.0.090213
7-240
Virtual Private Networks
Configure the VPN Client
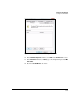
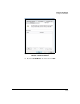
Figure 7-209. Windows Vista—Custom Security
Method Settings Window
42. In the Custom Security Method Settings window, select settings that match
the IPsec proposal and IPsec policy settings on the TMS zl Module:
a. Select the Data integrity and encryption (ESP) check box.
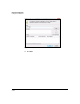
b. For Integrity algorithm, match the authentication algorithm in the
module’s IPsec proposal.
c. For Encryption algorithm, match the encryption algorithm in the mod-
ule’s IPsec proposal.
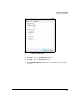
d. If you configured an SA lifetime in kilobytes in the module’s IPsec
policy, under Session key settings, select the Generate a new key every
check box on the left. Then type the matching number in the box
below.
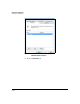
e. If you configured an SA lifetime in seconds in the module’s IPsec
policy, under Session key settings, select the Generate a new key every
check box on the right. Then type the matching number in the box
below.
Table 7-17 displays the default settings for an IPsec proposal and IPsec
policy on the TMS zl Module.