TMS zl Management and Configuration Guide ST.1.0.090213
7-245
Virtual Private Networks
Configure the VPN Client
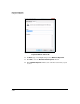
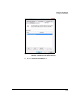
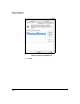
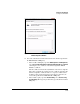
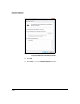
Figure 7-214. Windows Vista—Edit Authentication
Method Properties Window
51. Select the authentication method that matches the method specified in
the TMS zl Module’s IKE policy:
• If the module’ s IKE policy specifies RSA Signature or DSA Signature,
select Use a certificate from this certification authority (CA). Click Browse
and navigate to the certificate of the CA that signed the TMS zl
Module’s certificate.
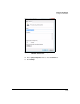
The CA certificate must be already installed on the remote endpoint.
The remote endpoint also requires its own certificate signed by this
CA. The endpoint’s certificate must be a computer certificate that
includes a subject name that matches, in both type and value, the
remote ID specified in the TMS zl Module’s IKE policy.
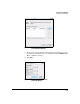
• If the module’s policy specifies Preshared Key, select Use this string
(preshared key). Then type the preshared key specified in the module’s
IKE policy.