TMS zl Management and Configuration Guide ST.1.0.090213
7-250
Virtual Private Networks
Configure the VPN Client
61. Configure settings to match the settings in the TMS zl Module’s IKE policy:
a. For Integrity algorithm, match the module’s IKE authentication algo-
rithm setting.
b. For Encryption algorithm, match the module’s IKE encryption algo-
rithm setting.
c. For Diffie-Hellman Group, match the module’s DH group setting.
Table 7-18 displays the default settings for a TMS zl Module IKE policy.
Table 7-18. Default TMS zl Module IKE Settings
d. Click OK to close the IKE Security Algorithms window.
A message might be displayed, informing you that your choices are not
the most secure. Click Yes.
62. Click OK to close the Key Exchange Security Methods window.
63. Click OK to close the Key Exchange Settings window.
64. Click OK to close the <policy> Properties window.
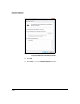
65. Right-click the policy that you just created and click Assign to start
enforcing the IPsec policy.
Figure 7-220. Windows Vista—Local Security Settings Window (Assign the Policy)
66. Click Start > Control Panel.
Parameter Default Setting
Authentication Algorithm MD5
Encryption Algorithm 3DES
Diffie-Hellman (DH) Group 1