TMS zl Management and Configuration Guide ST.1.1.100226
7-53
Virtual Private Networks
Configure an IPsec Client-to-Site VPN
You can, of course, configure other objects that are appropriate for your
environment. And you might choose not to configure some of the objects. For
example, you might not know the actual IP address of every remote VPN client,
particularly when remote users connect through the Internet. Or the IP
addresses might not be contiguous, preventing you from placing them in a
single-entry object (which required for address objects used in VPNs).
Create an IPsec Proposal
Each IPsec proposal specifies the following:
■ IPsec mode (tunnel or transport)
■ IPsec security protocol:
• AH and a single authentication algorithm
• ESP, a single authentication algorithm, and a single encryption
algorithm
You can configure multiple IPsec proposals. In a later task, you will specify a
proposal in an IPsec policy. The algorithm or algorithms in that proposal will
secure traffic that is part of IPsec tunnels (VPN connections) that are estab-
lished with that policy.
Follow these steps to configure an IPsec proposal:
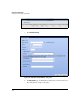
1. In the left navigation bar of the Web browser interface, click VPN > IPsec.
2. Click the IPsec Proposals tab.
Figure 7-41. VPN > IPsec > IPsec Proposals Window
3. Click Add IPsec Proposal. The Add IPsec Proposal window is displayed.