TMS zl Management and Configuration Guide ST.1.1.100226
7-54
Virtual Private Networks
Configure an IPsec Client-to-Site VPN
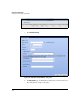
Figure 7-42. Add IPsec Proposal Window
4. For Proposal Name, type a descriptive string of 1 to 32 alphanumeric
characters. The string must be unique to this proposal.
Often, it is a good idea to indicate the algorithms that you will select in
the name—for example, ESP3desMD5.
5. For Encapsulation Mode, typically select Tunnel Mode.
Tunnel mode allows remote endpoints to reach services behind the TMS
zl Module. In transport mode, the VPN only supports traffic originated by
the remote endpoint or by the TMS zl Module itself. Therefore, this mode
is typically used when you are creating a proposal for GRE over IPsec site-
to-site VPNs or L2TP over IPsec client-to-site VPNs.
6. For Security Protocol, select AH or ESP.
7. If you selected ESP in the previous step, select one of the following for
Encryption Algorithm:
•NULL
If you select this option, VPN traffic will not be encrypted.
•DES
•3DES
• AES-128 (16)
• AES-192 (24)
• AES-256 (32)
The number in parentheses after AES options indicates the key length for
the algorithm in bytes.