TMS zl Module Planning and Implementation Guide 2009-08
Table Of Contents
- Contents
- Glossary of Acronyms and Abbreviations
- 1.0 Purpose
- 2.0 Intended Audience
- 3.0 Objectives
- 4.0 Prerequisites
- 5.0 Skills
- 6.0 The HP ProCurve Threat Management Services zl Module
- 7.0 Common TMS Security Control Points
- 8.0 Deployment Considerations
- 9.0 Installation and Preparation of the TMS zl Module
- 10.0 Configuration of the TMS zl Module
- 11.0 Using multiple HP ProCurve Threat Management Services zl Modules
- Appendix A – Additional References
- Appendix B – Sample Company Information Assets Spreadsheet
- Sample “Information Assets” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Server Network Details” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “TMS Zones” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Firewall Rules” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- /Sample “Company Information Assets” Microsoft Excel 2003 spreadsheet
- Appendix C – Information Gathering Tools
- Appendix D - Updating Switch Software
- Appendix E – Emergency Recovery Process
Page 11
• Reusability of firewall policies, for example in the VPN control
• Selective application of IPS by individual firewall rules
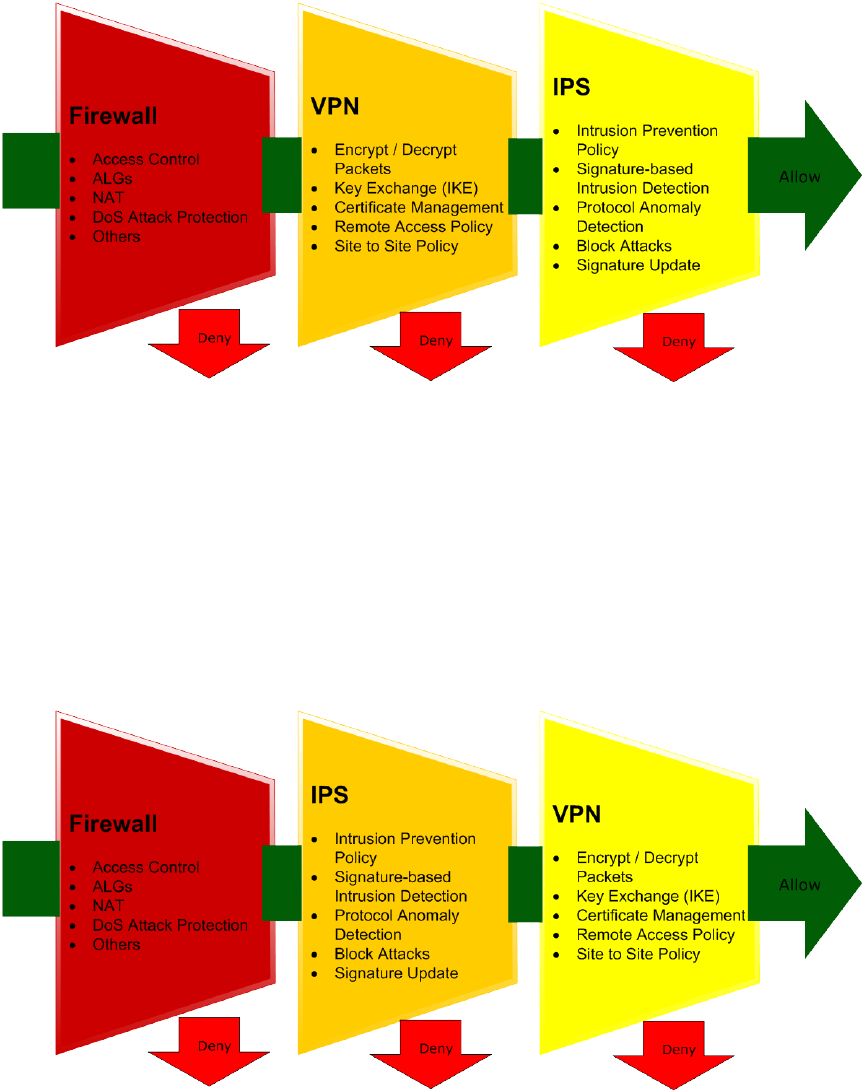
The following diagram shows the order of processing by the three controls on traffic
incoming to a TMS zl Module zone interface:
Figure 1: TMS zl Module Interface Inbound Processing Flow
Packets inbound on an interface are first processed by the firewall. If they are permitted
by the security policy rules, then they will pass to the VPN Gateway for decryption, if
necessary. Finally, now that even originally encrypted traffic is in the clear, the Intrusion
Prevention System will inspect the packet for malicious activity signatures, specific
protocol anomalies and general IP anomalies. At any of these three processing stages, the
traffic is subject to either being summarily dropped or having its connection reset if it is
found to be outside of configured security policy rules.
The order of processing is slightly different for traffic exiting the TMS zl Module on one
of its zone interfaces:
Figure 2: TMS zl Module Interface Outbound Processing Flow










