TMS zl Module Planning and Implementation Guide 2009-08
Table Of Contents
- Contents
- Glossary of Acronyms and Abbreviations
- 1.0 Purpose
- 2.0 Intended Audience
- 3.0 Objectives
- 4.0 Prerequisites
- 5.0 Skills
- 6.0 The HP ProCurve Threat Management Services zl Module
- 7.0 Common TMS Security Control Points
- 8.0 Deployment Considerations
- 9.0 Installation and Preparation of the TMS zl Module
- 10.0 Configuration of the TMS zl Module
- 11.0 Using multiple HP ProCurve Threat Management Services zl Modules
- Appendix A – Additional References
- Appendix B – Sample Company Information Assets Spreadsheet
- Sample “Information Assets” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Server Network Details” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “TMS Zones” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Firewall Rules” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- /Sample “Company Information Assets” Microsoft Excel 2003 spreadsheet
- Appendix C – Information Gathering Tools
- Appendix D - Updating Switch Software
- Appendix E – Emergency Recovery Process
Page 114
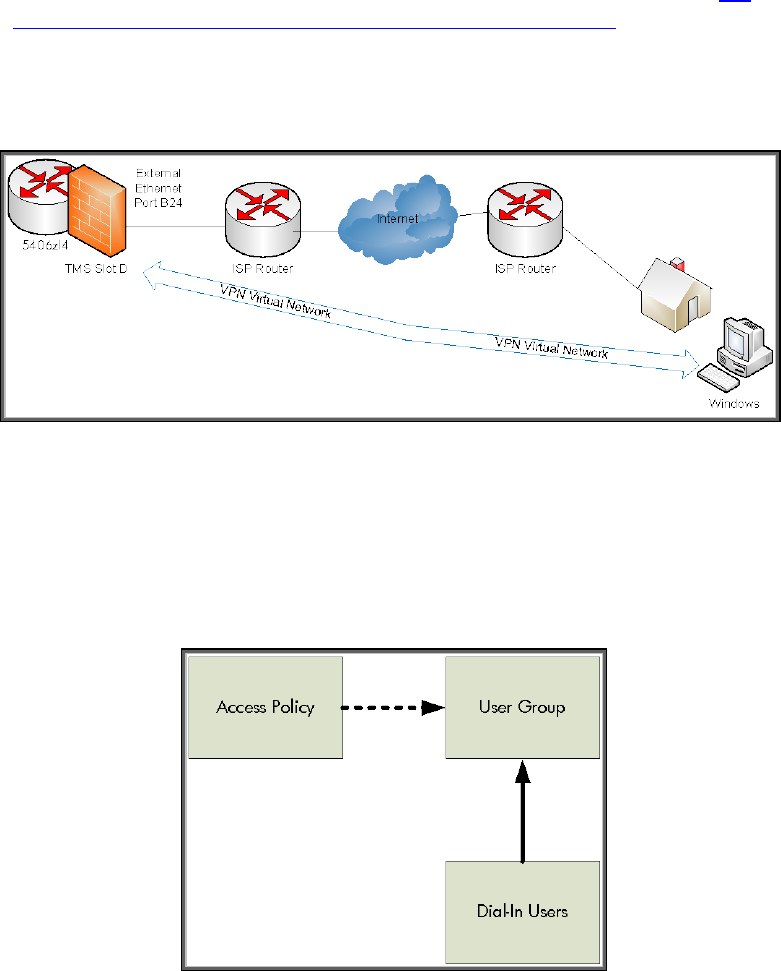
10.5.5 Remote Access with Windows and L2TP over IPsec
Let’s examine our next VPN scenario – the remote worker “dialing in” to
access resources at the main office. This section will detail the TMS zl
Module configuration. Detailed configuration for Windows XP and Vista
clients will not be discussed in this section. For more discussion on
configuration Windows and Macintosh VPN clients, see Section C in the HP
ProCurve Threat Management Solution Implementation Guide.
This diagram is very similar to the site-to-site diagram except we only have
one TMS zl Module. The protection needs haven’t changed – we still need to
protect the traffic over the Internet.
Figure 25
We will be specifying firewall access policies on the basis of group
membership. Users are specified on the TMS zl Module and are required to be
associated with a Group. When a user successfully “VPNs” into the TMS zl
Module, their group membership is determined and the access policies
associated to that group are put in place.
Figure 26