TMS zl Module Planning and Implementation Guide 2009-08
Table Of Contents
- Contents
- Glossary of Acronyms and Abbreviations
- 1.0 Purpose
- 2.0 Intended Audience
- 3.0 Objectives
- 4.0 Prerequisites
- 5.0 Skills
- 6.0 The HP ProCurve Threat Management Services zl Module
- 7.0 Common TMS Security Control Points
- 8.0 Deployment Considerations
- 9.0 Installation and Preparation of the TMS zl Module
- 10.0 Configuration of the TMS zl Module
- 11.0 Using multiple HP ProCurve Threat Management Services zl Modules
- Appendix A – Additional References
- Appendix B – Sample Company Information Assets Spreadsheet
- Sample “Information Assets” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Server Network Details” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “TMS Zones” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Firewall Rules” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- /Sample “Company Information Assets” Microsoft Excel 2003 spreadsheet
- Appendix C – Information Gathering Tools
- Appendix D - Updating Switch Software
- Appendix E – Emergency Recovery Process
Page 128
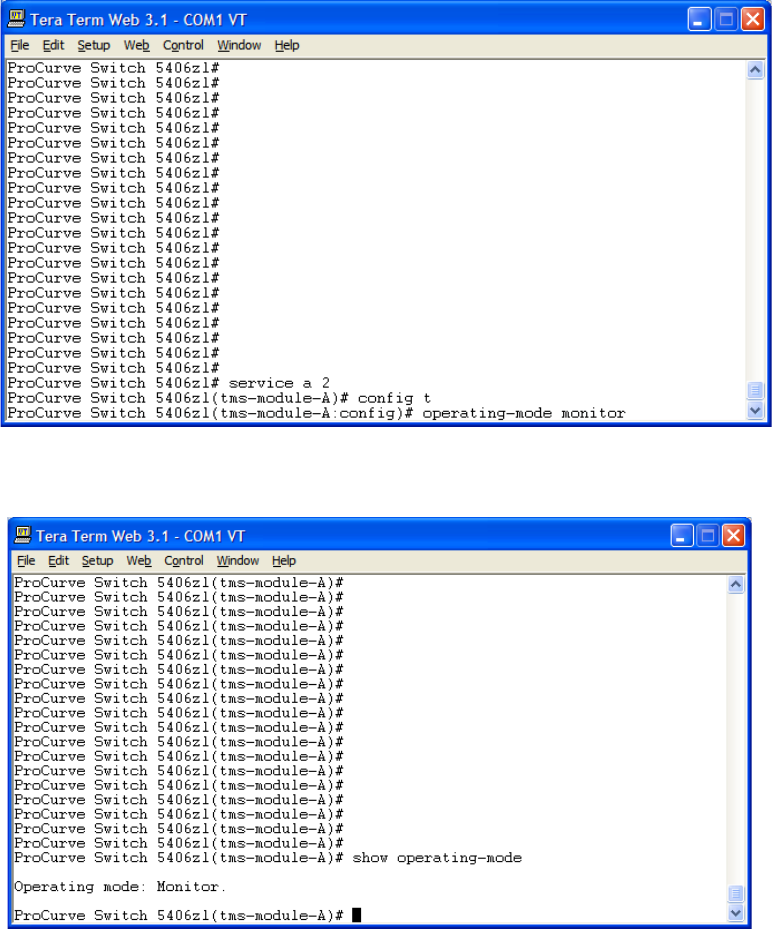
Next, let’s change the operating mode of the TMS zl Module in Slot A to “monitor”.
This will require a reboot of this TMS zl Module. The default operating mode of the
TMS zl Module is “routing”.
Once rebooted, let’s double check the operating mode. As we can see, it is in monitor.
We can now begin our configuration.