TMS zl Module Planning and Implementation Guide 2009-08
Table Of Contents
- Contents
- Glossary of Acronyms and Abbreviations
- 1.0 Purpose
- 2.0 Intended Audience
- 3.0 Objectives
- 4.0 Prerequisites
- 5.0 Skills
- 6.0 The HP ProCurve Threat Management Services zl Module
- 7.0 Common TMS Security Control Points
- 8.0 Deployment Considerations
- 9.0 Installation and Preparation of the TMS zl Module
- 10.0 Configuration of the TMS zl Module
- 11.0 Using multiple HP ProCurve Threat Management Services zl Modules
- Appendix A – Additional References
- Appendix B – Sample Company Information Assets Spreadsheet
- Sample “Information Assets” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Server Network Details” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “TMS Zones” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Firewall Rules” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- /Sample “Company Information Assets” Microsoft Excel 2003 spreadsheet
- Appendix C – Information Gathering Tools
- Appendix D - Updating Switch Software
- Appendix E – Emergency Recovery Process
Page 3
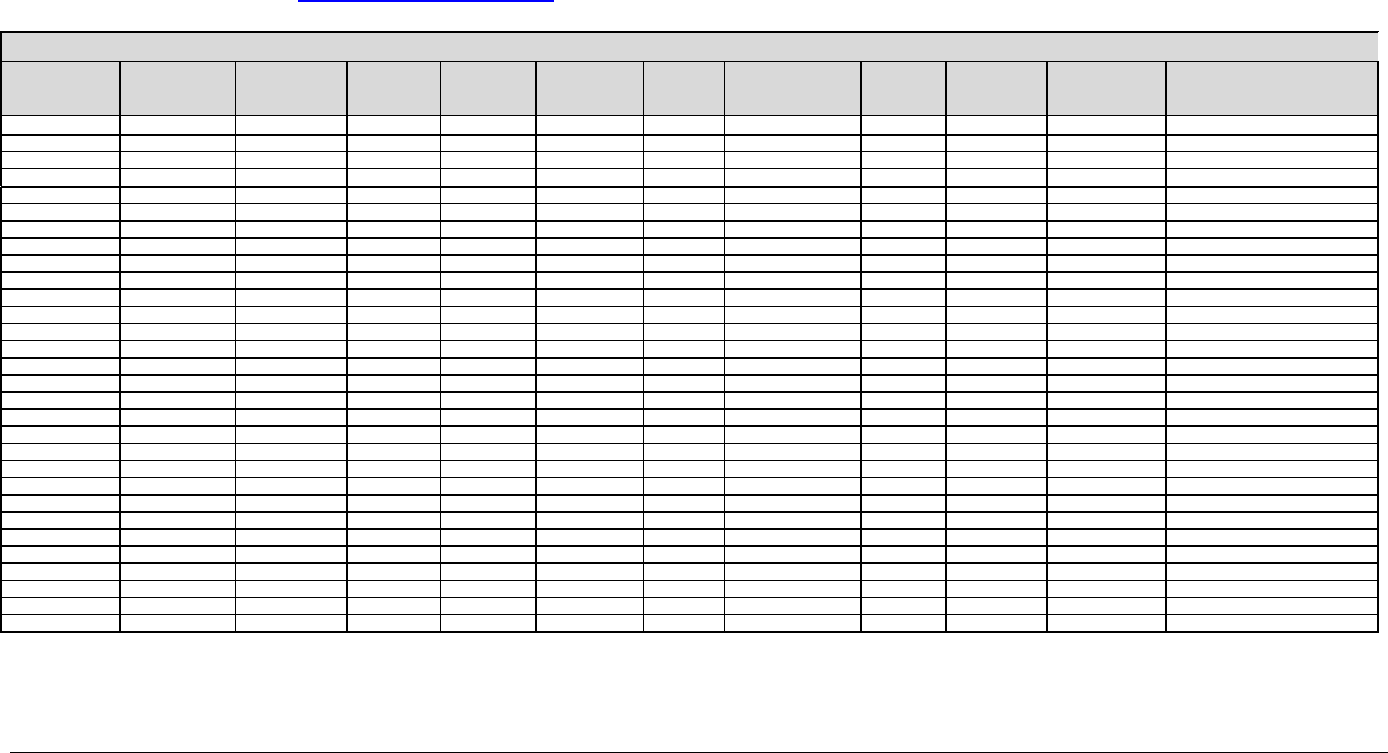
“Firewall Rules” tab (See “Company Information Assets” Microsoft Excel 2003 spreadsheet)
Information Asset Source Zone Destination Zone Protocol
Source Port
#(s)
Source Address
(Optional)
Destination
Port #(s)
Destination Address
(Optional)
Action Schedule
Rate
(KB, Packets,
Connections)
Comments
MS Dynamics Internal Internal TCP 1433 10.4.20.52/16 1433 10.20.10.25/16 Permit Always N/A To Database server
MS Dynamics Internal Zone3 TCP 2712 10.4.20.52/16 2712 All Permit M-F, 6AM-6PM N/A To Wired end usersVLAN
Mail External Internal TCP 25 All 25 10.5.15.25/16 Permit Always N/A External Email access
Mail Internal External TCP 25 10.5.15.25/16 25 All Permit Always N/A External Email access
Customer Sign-off
Zone Firewall Rules
I agree that this Zone Firewall Rules document accurately captures all “High-risk” and “Confidential” information assets that require protection as part of the TMS zl firewall implementation project
performed by __________________________________.
(Professional Services Provider)
_________________________________________________
____/____/_______
(Customer IT Director)
(Date)










