TMS zl Module Planning and Implementation Guide 2009-08
Table Of Contents
- Contents
- Glossary of Acronyms and Abbreviations
- 1.0 Purpose
- 2.0 Intended Audience
- 3.0 Objectives
- 4.0 Prerequisites
- 5.0 Skills
- 6.0 The HP ProCurve Threat Management Services zl Module
- 7.0 Common TMS Security Control Points
- 8.0 Deployment Considerations
- 9.0 Installation and Preparation of the TMS zl Module
- 10.0 Configuration of the TMS zl Module
- 11.0 Using multiple HP ProCurve Threat Management Services zl Modules
- Appendix A – Additional References
- Appendix B – Sample Company Information Assets Spreadsheet
- Sample “Information Assets” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Server Network Details” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “TMS Zones” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Firewall Rules” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- /Sample “Company Information Assets” Microsoft Excel 2003 spreadsheet
- Appendix C – Information Gathering Tools
- Appendix D - Updating Switch Software
- Appendix E – Emergency Recovery Process
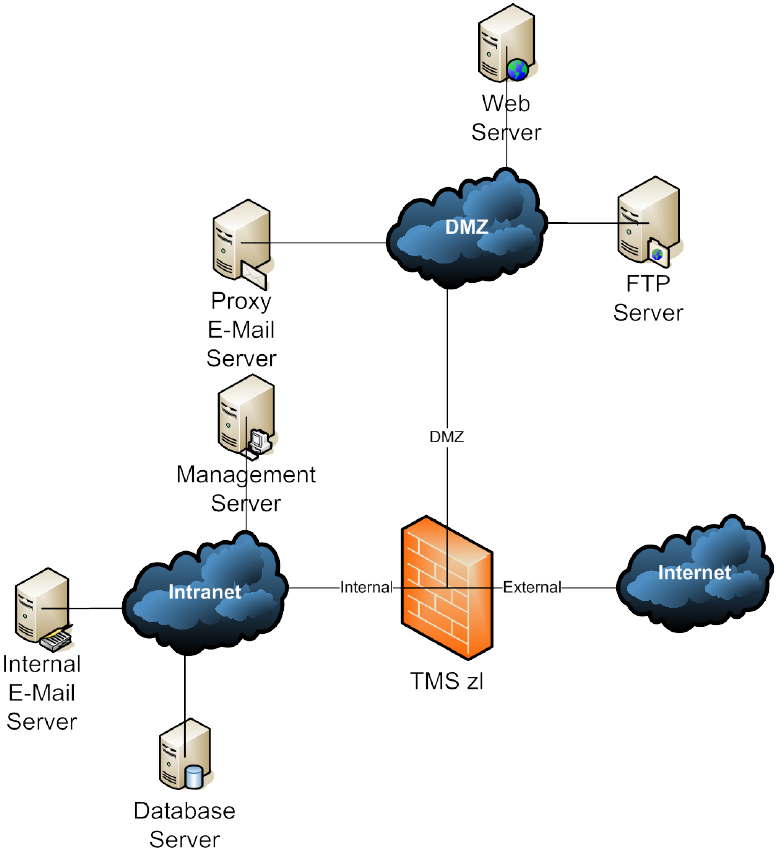
Page 15
Figure 3: Perimeter Security Control Point
At this control point, as shown in Figure 3, the HP ProCurve Threat Management
Services zl Module can:
• Restrict inbound traffic with the firewall feature to only that which is absolutely
necessary for the services and applications the organization wishes to intentionally
expose, perform NAT, and restrict outbound traffic determined necessary to conduct
business.
• Inspect the traffic permitted to pass through with the intrusion detection / prevention
feature for malicious intrusion signatures and either report suspicious activity when
operating as an IDS or take preventive measures, such as logging and/or dropping
the suspicious packets, when operating as an IPS
• Act as a Remote Access VPN Gateway for teleworkers or a site-to-site VPN
Gateway for connections to remote offices or business partners via tunnels through
the Internet










