TMS zl Module Planning and Implementation Guide 2009-08
Table Of Contents
- Contents
- Glossary of Acronyms and Abbreviations
- 1.0 Purpose
- 2.0 Intended Audience
- 3.0 Objectives
- 4.0 Prerequisites
- 5.0 Skills
- 6.0 The HP ProCurve Threat Management Services zl Module
- 7.0 Common TMS Security Control Points
- 8.0 Deployment Considerations
- 9.0 Installation and Preparation of the TMS zl Module
- 10.0 Configuration of the TMS zl Module
- 11.0 Using multiple HP ProCurve Threat Management Services zl Modules
- Appendix A – Additional References
- Appendix B – Sample Company Information Assets Spreadsheet
- Sample “Information Assets” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Server Network Details” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “TMS Zones” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Firewall Rules” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- /Sample “Company Information Assets” Microsoft Excel 2003 spreadsheet
- Appendix C – Information Gathering Tools
- Appendix D - Updating Switch Software
- Appendix E – Emergency Recovery Process
Page 5
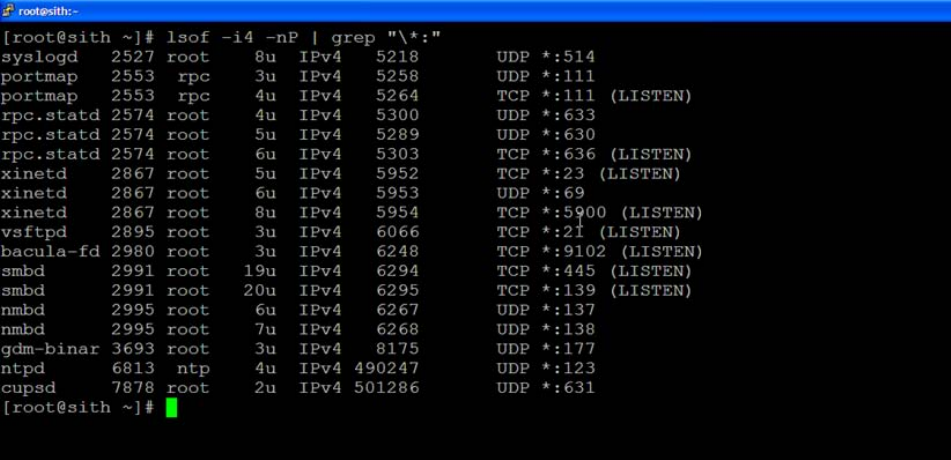
lsof
lsof is a utility included in Unix and Unix-like operating systems that is used for listing the open
files on the system. The following screenshot shows the utility invoked with the -i4 (display
internet protocol version 4 network files), -n (numeric addresses, which suppresses attempts to
convert IP addresses to host names), and -P (Port numbers, which suppresses attempts to convert
port numbers to service names). The options are being “piped” through the grep utility, which is
used to print lines matching a pattern (in this case a literal asterisk character, not a wildcard as
indicated by the preceding backslash, followed by a colon character).
The columns of interest for the purposes of this document are:
COMMAND (1
st
column) – Provides the name of the executable file for the process
PID (2
nd
column) – Displays the Process ID of the process
USER (3
rd
column) – Shows the User ID that the process is executing as. Processes
executing as the root user are of particular interest as they are executing with
unlimited, “super-user” privileges.
NODE (8
th
column) – Indicates whether the network “file” is TCP or UDP
NAME (9
th
column) – Details the local IP address(es) the process is associated with
and the port number of the TCP listener or UDP port
Screen shot of lsof -i4 -nP | grep “\*:” showing results that detail processes, process IDs,
execution privilege levels and associated open TCP listener or UDP ports.










