TMS zl Module Planning and Implementation Guide 2009-08
Table Of Contents
- Contents
- Glossary of Acronyms and Abbreviations
- 1.0 Purpose
- 2.0 Intended Audience
- 3.0 Objectives
- 4.0 Prerequisites
- 5.0 Skills
- 6.0 The HP ProCurve Threat Management Services zl Module
- 7.0 Common TMS Security Control Points
- 8.0 Deployment Considerations
- 9.0 Installation and Preparation of the TMS zl Module
- 10.0 Configuration of the TMS zl Module
- 11.0 Using multiple HP ProCurve Threat Management Services zl Modules
- Appendix A – Additional References
- Appendix B – Sample Company Information Assets Spreadsheet
- Sample “Information Assets” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Server Network Details” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “TMS Zones” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Firewall Rules” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- /Sample “Company Information Assets” Microsoft Excel 2003 spreadsheet
- Appendix C – Information Gathering Tools
- Appendix D - Updating Switch Software
- Appendix E – Emergency Recovery Process
Page 20
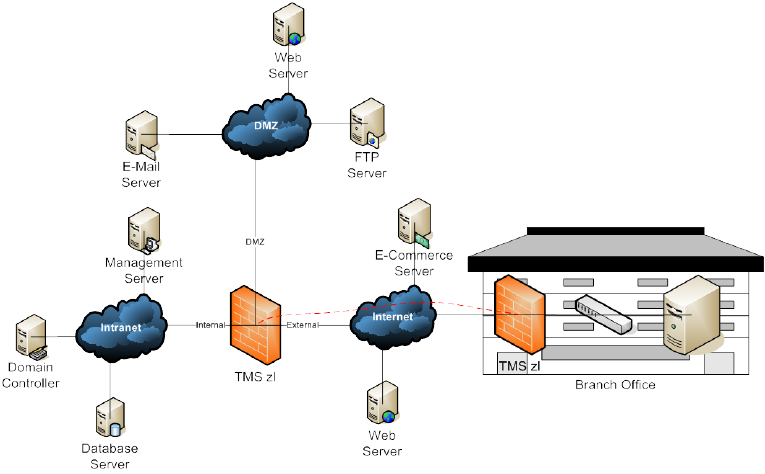
Figure 5: Perimeter Security Control Point site-to-site VPN
Typical controls implemented by VPN Gateways are:
• Authentication via Xauth against an internal, local list, RADIUS
• Source authentication and data integrity through Authentication Header
(IPsec AH)
• Source authentication, data integrity and confidentiality using
Encapsulating Security Payload (IPsec ESP)
• Anti-replay with configurable window size of acceptable sequence
number difference
7.2 Data Center Security Enclave
The data center, with its concentration of high-value information assets, is another
increasingly common place to layer in additional security controls. The TMS zl Module
can be added to the data center to perform compartmentalization of the different servers
and services that they offer. When located at the boundary between the data center and
the rest of the enterprise network, it can turn the entire data center into a security enclave,
or it can be placed in such a way as to perform both functions as shown in Figure 6:










