TMS zl Module Planning and Implementation Guide 2009-08
Table Of Contents
- Contents
- Glossary of Acronyms and Abbreviations
- 1.0 Purpose
- 2.0 Intended Audience
- 3.0 Objectives
- 4.0 Prerequisites
- 5.0 Skills
- 6.0 The HP ProCurve Threat Management Services zl Module
- 7.0 Common TMS Security Control Points
- 8.0 Deployment Considerations
- 9.0 Installation and Preparation of the TMS zl Module
- 10.0 Configuration of the TMS zl Module
- 11.0 Using multiple HP ProCurve Threat Management Services zl Modules
- Appendix A – Additional References
- Appendix B – Sample Company Information Assets Spreadsheet
- Sample “Information Assets” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Server Network Details” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “TMS Zones” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Firewall Rules” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- /Sample “Company Information Assets” Microsoft Excel 2003 spreadsheet
- Appendix C – Information Gathering Tools
- Appendix D - Updating Switch Software
- Appendix E – Emergency Recovery Process
Page 22
LDAP traffic bound for the Domain Controllers, SQL traffic aimed at the Database
Servers, and any application-specific traffic intended for the Application Servers.
• Employ the intrusion detection / prevention feature to either alert administrators or
interrupt suspicious traffic signatures, protocol-specific anomalies and general
network anomalies appearing within conversations that pass the data center enclave
firewall or between the compartmentalized zones within the data center.
• Utilize the VPN Gateway feature to terminate tunnels that must come directly into
the data center. For example, an “Extranet” connection to a strategic partner whose
internal address space overlaps with a portion of the enterprise network’s address
space, but not the data center’s address space that is enabling collaboration on
highly sensitive research and development with details that must be protected even
from the majority of the enterprise’s internal users.
7.2.1 Firewall
Depending on whether the data center is compartmentalized into separate
zones or not, the following 2 scenarios of typical controls implemented by
firewalls in the data center include, but are not limited to the following:
Scenario 1 - Typical firewall controls for a data center compartmentalized
in zones as in Figure 6, above:
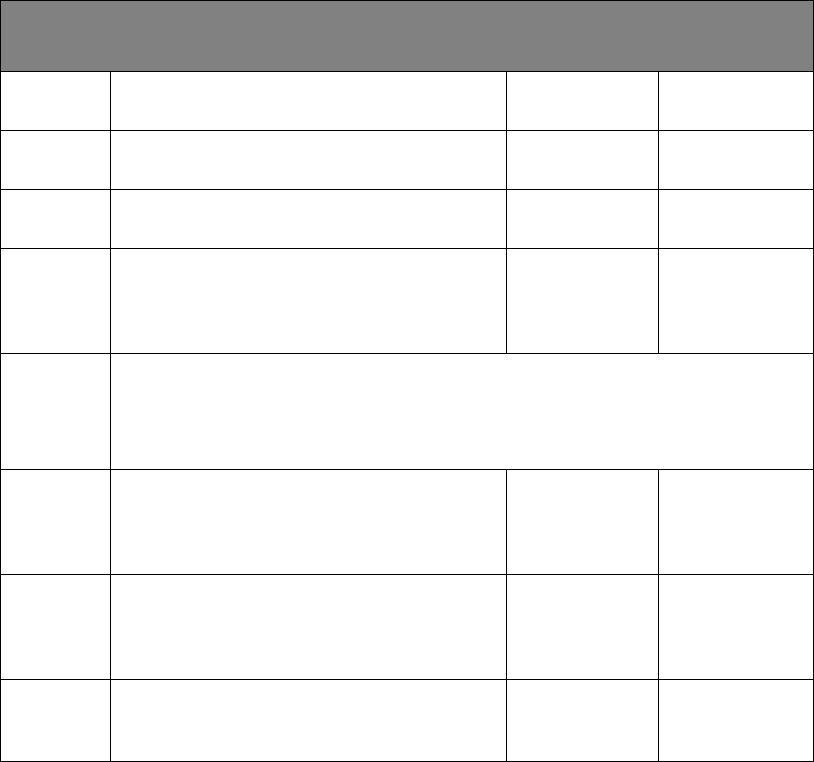
Action
Description
From Zone
(Source)
To Zone
(Destination)
Permit
Simple Network Management Protocol
(SNMP) Traps (UDP/162)
External
Management
Permit
Server Message Block (SMB, UDP/135-139,
445 and TCP/135-139, 445)
External
SMB
Permit
Active Directory (AD, UDP/42, 53, 88, 135,
137, 138, 389, 445, 1512 and TCP/42, 53, 88,
135, 137, 139, 389, 445, 636, 1512, 3268,
3269, AD-fixed-port, FRS-fixed-port)
External
AD
Note: DS-fixed-port and FRS-fixed-port require registry changes on all Global
Catalog, Domain Controller and Member Servers to fix the Directory Services and
File Replication Service ports to single ports vs. the default behavior of fully
dynamic Remote Procedure Call (RPC) that would require TCP/1024-65535 to be
opened.
Permit
Structured Query Language (SQL, TCP/1433
[SQL Server], 1521 [Oracle], 1533 [Informix],
2638 [Sybase], 3306 [mySQL], 5432
[PostgreSQL])
External
SQL
Permit
Unity (UDP/137, 138, 5000-5020, 22800-
32767 and TCP/80, 135, 139, 443, 445, 3389,
5000-5020, 5060, 5900) and Citrix (TCP/80,
443, 1494, 1604)
External
Apps
Deny
All other traffic
External
AD, Apps,
Management,
SMB, SQL










