TMS zl Module Planning and Implementation Guide 2009-08
Table Of Contents
- Contents
- Glossary of Acronyms and Abbreviations
- 1.0 Purpose
- 2.0 Intended Audience
- 3.0 Objectives
- 4.0 Prerequisites
- 5.0 Skills
- 6.0 The HP ProCurve Threat Management Services zl Module
- 7.0 Common TMS Security Control Points
- 8.0 Deployment Considerations
- 9.0 Installation and Preparation of the TMS zl Module
- 10.0 Configuration of the TMS zl Module
- 11.0 Using multiple HP ProCurve Threat Management Services zl Modules
- Appendix A – Additional References
- Appendix B – Sample Company Information Assets Spreadsheet
- Sample “Information Assets” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Server Network Details” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “TMS Zones” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Firewall Rules” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- /Sample “Company Information Assets” Microsoft Excel 2003 spreadsheet
- Appendix C – Information Gathering Tools
- Appendix D - Updating Switch Software
- Appendix E – Emergency Recovery Process
Page 27
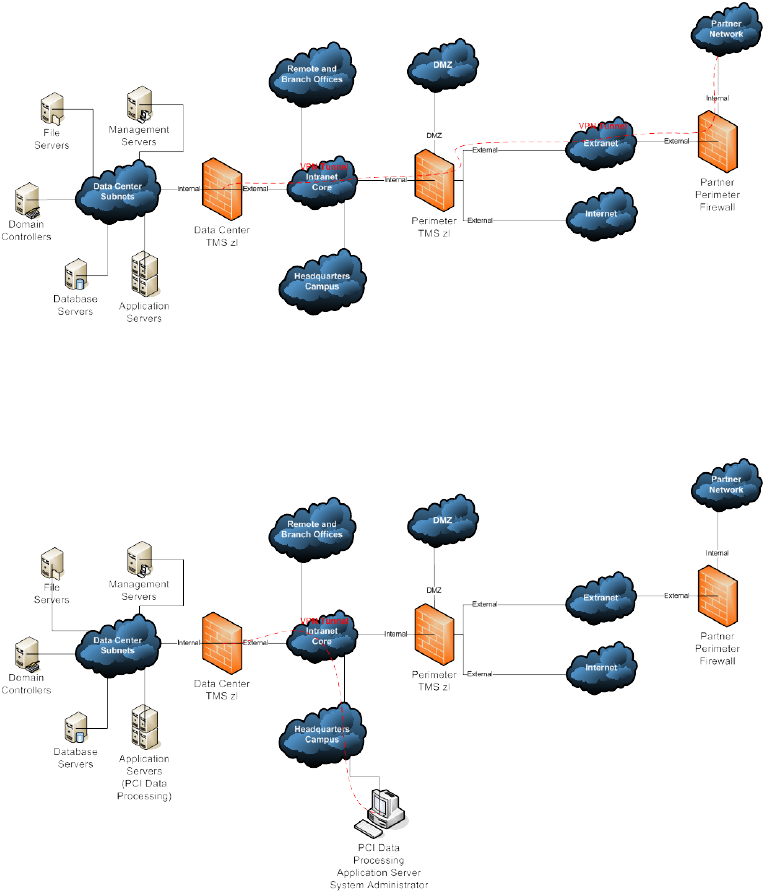
7.2.3 VPN Gateway
The TMS zl Module is shown in Figure 8 performing as a site-to-site VPN
Gateway for a strategic business partner, providing an additional layer of
security to an extranet connection. The perimeter firewall is simply a pass-
through point in the VPN tunnel’s path. Any NAT performed by the perimeter
firewall is dealt with through the use of the standard NAT Traversal (NAT-T)
option.
Note: Terminating the tunnel directly in the data center reduces the
partner’s access to the remainder of the enterprise network and also
protects the traffic from potential eavesdropping in the remainder of the
enterprise network, e.g. highly sensitive research and development
activities, activities potentially subject to industrial espionage, etc.
Figure 8: Data Center Security Control Point Extranet VPN
Figure 9 below illustrates another common data center VPN scenario :
Figure 9: Data Center Security Control Point Internal VPN










