TMS zl Module Planning and Implementation Guide 2009-08
Table Of Contents
- Contents
- Glossary of Acronyms and Abbreviations
- 1.0 Purpose
- 2.0 Intended Audience
- 3.0 Objectives
- 4.0 Prerequisites
- 5.0 Skills
- 6.0 The HP ProCurve Threat Management Services zl Module
- 7.0 Common TMS Security Control Points
- 8.0 Deployment Considerations
- 9.0 Installation and Preparation of the TMS zl Module
- 10.0 Configuration of the TMS zl Module
- 11.0 Using multiple HP ProCurve Threat Management Services zl Modules
- Appendix A – Additional References
- Appendix B – Sample Company Information Assets Spreadsheet
- Sample “Information Assets” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Server Network Details” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “TMS Zones” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Firewall Rules” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- /Sample “Company Information Assets” Microsoft Excel 2003 spreadsheet
- Appendix C – Information Gathering Tools
- Appendix D - Updating Switch Software
- Appendix E – Emergency Recovery Process
Page 30
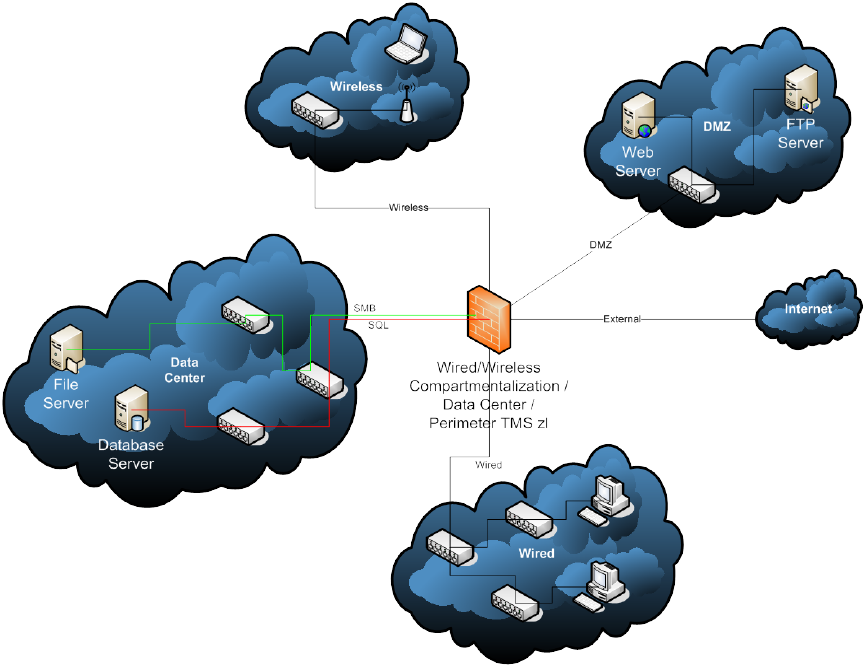
Figure 11: Wired/Wireless Compartmentalization / Data Center
Compartmentalization / Perimeter Security Control Point
Note: As in the previous figure, multiple LAN switches are depicted above for
visual clarity but the above topology could be implemented via a single physical
switch using separate VLANs for each of the “clouds” and two different VLANs
for the two distinct security zones shown within the Data Center “cloud.”
Figure 11, above, shows a variation on the previously shown scenario. It shows the TMS
zl Module acting as traditional perimeter security, compartmentalizing the wireless
portions of the network from the wired portions and adding additional security to the data
center, but this time there is additional compartmentalization within the data center by
server type. For example, file servers in one zone and database servers in a different
zone.
It is worth considering at this point that, while the above examples are careful to point out
that a single TMS zl Module is capable of simultaneously fulfilling all three of its most
common placement scenarios ( e.g. Perimeter, Data Center and Compartmentalization), it
is exceptionally uncommon for an enterprise network to not have redundant firewalls.
The TMS zl Module supports High Availability in Active-Standby configuration. There
is no requirement to purchase an additional TMS zl Module, but it is a best practice
recommended by HP ProCurve to avoid the single point of failure represented by only
having a single unit.










