TMS zl Module Planning and Implementation Guide 2009-08
Table Of Contents
- Contents
- Glossary of Acronyms and Abbreviations
- 1.0 Purpose
- 2.0 Intended Audience
- 3.0 Objectives
- 4.0 Prerequisites
- 5.0 Skills
- 6.0 The HP ProCurve Threat Management Services zl Module
- 7.0 Common TMS Security Control Points
- 8.0 Deployment Considerations
- 9.0 Installation and Preparation of the TMS zl Module
- 10.0 Configuration of the TMS zl Module
- 11.0 Using multiple HP ProCurve Threat Management Services zl Modules
- Appendix A – Additional References
- Appendix B – Sample Company Information Assets Spreadsheet
- Sample “Information Assets” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Server Network Details” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “TMS Zones” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Firewall Rules” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- /Sample “Company Information Assets” Microsoft Excel 2003 spreadsheet
- Appendix C – Information Gathering Tools
- Appendix D - Updating Switch Software
- Appendix E – Emergency Recovery Process
Page 35
the modification, regardless of the theoretical source and destination security
zones.
See Chapter 6, “Intrusion Detection and Prevention,” of the HP ProCurve
Threat Management Services zl Module Management and Configuration Guide
for detailed information on how to enable the intrusion subsystem, register
your signature update subscription, disable individual signatures and tune
protocol-specific anomaly settings. If absolutely necessary and the potential
risks are well-understood, steps are provided on how to modify the actions
taken for all intrusion signatures predefined for a given threat level.
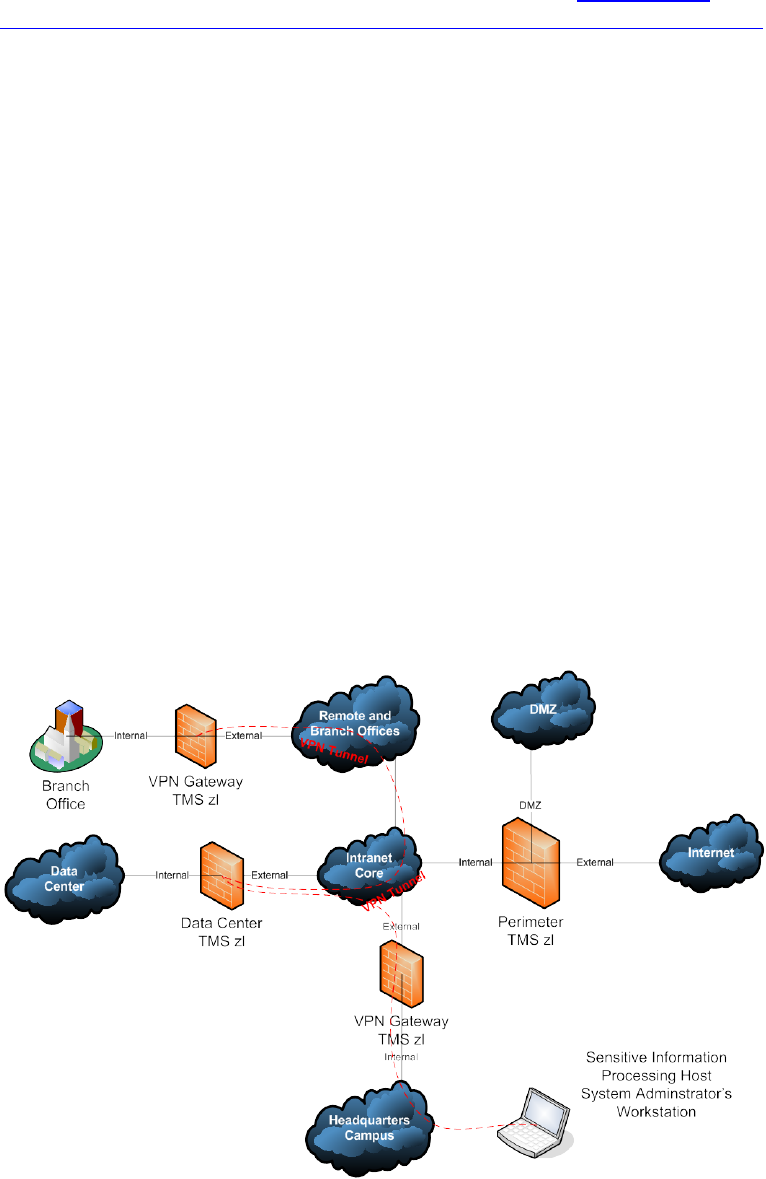
7.3.3 VPN Gateway
The following figure displays a compartmentalization usage for the TMS zl
Module’s VPN gateway security control feature. Regulatory compliance, such
as HIPAA Private Health Information (PHI), and industry self-regulation
directives, like the Payment Card Industry Data Security Standard (PCI DSS),
have made it an increasingly common business strategy for those organizations
affected to implement security enclaves at the application edge for sensitive
information. For example, “credit card swipe” point-of-sale machines in
remote stores can be connected via encrypted VPN tunnels over the enterprise
network to another security enclave for the hosts in the organization’s data
center that process this sensitive information. In its simplest conceptual form,
this is a sensitive information compartment connected to another sensitive
information compartment via an encrypted tunnel, effectively creating a
sensitive information “overlay” network on top of the overall enterprise
network.
Figure 15: Compartmentalization Security Control Point(s) VPN










