TMS zl Module Planning and Implementation Guide 2009-08
Table Of Contents
- Contents
- Glossary of Acronyms and Abbreviations
- 1.0 Purpose
- 2.0 Intended Audience
- 3.0 Objectives
- 4.0 Prerequisites
- 5.0 Skills
- 6.0 The HP ProCurve Threat Management Services zl Module
- 7.0 Common TMS Security Control Points
- 8.0 Deployment Considerations
- 9.0 Installation and Preparation of the TMS zl Module
- 10.0 Configuration of the TMS zl Module
- 11.0 Using multiple HP ProCurve Threat Management Services zl Modules
- Appendix A – Additional References
- Appendix B – Sample Company Information Assets Spreadsheet
- Sample “Information Assets” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Server Network Details” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “TMS Zones” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Firewall Rules” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- /Sample “Company Information Assets” Microsoft Excel 2003 spreadsheet
- Appendix C – Information Gathering Tools
- Appendix D - Updating Switch Software
- Appendix E – Emergency Recovery Process
Page 4
10.1 Network Diagrams .................................................................................................................. 61
10.2 Switch Configuration .............................................................................................................. 63
10.3 Management VLAN and Zone ............................................................................................... 65
10.4 Zones to VLANs ..................................................................................................................... 70
10.5 Routing Mode ......................................................................................................................... 74
10.5.1 Firewall ............................................................................................................................... 74
10.5.2 IDS/IPS ............................................................................................................................... 83
10.5.3 Internet Access for Windows Update ................................................................................. 89
10.5.4 VPN Gateway ..................................................................................................................... 92
10.5.5 Remote Access with Windows and L2TP over IPsec ....................................................... 114
10.6 Monitor Mode ....................................................................................................................... 126
11.0 Using multiple HP ProCurve Threat Management Services zl Modules ................................... 136
11.1 Perimeter IDS and IPS ......................................................................................................... 136
11.2 Multinational Compartmentalization .................................................................................... 136
11.3 High Availability .................................................................................................................. 137
11.3.1 Configuring High Availability .......................................................................................... 139
Appendix A – Additional References ..................................................................................................... 141
Appendix B – Sample Company Information Assets Spreadsheet ............................................................. 1
Appendix C – Information Gathering Tools ............................................................................................... 1
Appendix D - Updating Switch Software ................................................................................................... 6
Appendix E – Emergency Recovery Process............................................................................................ 16
Table of Tables
Table 1: Glossary of Acronyms and Abbreviations .............................................................................. 4
Table 2: Named Objects and Their Uses .............................................................................................. 13
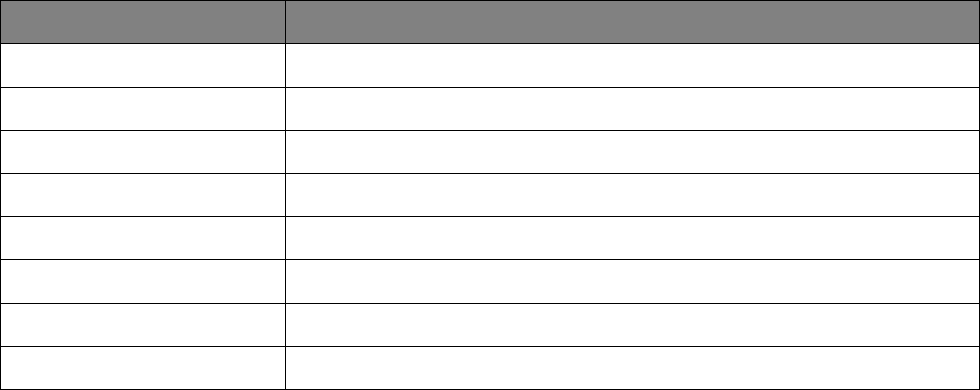
Table 1: Glossary of Acronyms and Abbreviations
Acronym / Abbreviation Meaning
HA
High Availability
IDS
Intrusion Detection System
IPS
Intrusion Prevention System
NAT
Network Address Translation
SPI
Stateful Packet Inspection
TMS
Threat Management Services
VPN
Virtual Private Network
VRRP
Virtual Router Redundancy Protocol










