TMS zl Module Planning and Implementation Guide 2009-08
Table Of Contents
- Contents
- Glossary of Acronyms and Abbreviations
- 1.0 Purpose
- 2.0 Intended Audience
- 3.0 Objectives
- 4.0 Prerequisites
- 5.0 Skills
- 6.0 The HP ProCurve Threat Management Services zl Module
- 7.0 Common TMS Security Control Points
- 8.0 Deployment Considerations
- 9.0 Installation and Preparation of the TMS zl Module
- 10.0 Configuration of the TMS zl Module
- 11.0 Using multiple HP ProCurve Threat Management Services zl Modules
- Appendix A – Additional References
- Appendix B – Sample Company Information Assets Spreadsheet
- Sample “Information Assets” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Server Network Details” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “TMS Zones” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Firewall Rules” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- /Sample “Company Information Assets” Microsoft Excel 2003 spreadsheet
- Appendix C – Information Gathering Tools
- Appendix D - Updating Switch Software
- Appendix E – Emergency Recovery Process
Page 41
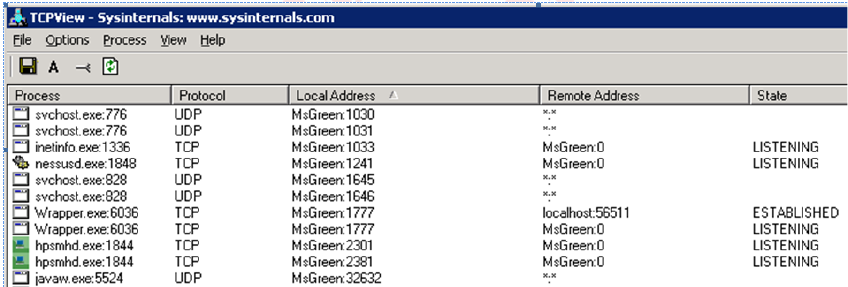
This is a sample of what TCP View will show for each process using TCP/IP on the
server:
Next, determine the related application or purpose of the specific process. This can be
performed by various means that could include:
• TCP View Properties (double-clicking a process)
• Process Explorer (double-clicking a process or Right-click and select Search
Online)
• Standard Internet search for the process
• Reviewing application manuals
• Reviewing the application’s web and/or support site
• Contacting the applications’ vendor
After researching each process, make sure to note the appropriate details. This step
needs to be repeated for each server.
8.5 Designing Security Controls
It should be apparent by now that we have been gathering the specific details and
requirements to set the groundwork for creating our final list of security controls to
implement. It is important that sufficient depth of research was performed during each of
the previous steps to ensure that the foundational information is complete and accurate
before taking these final steps.
Next we need to define the required TMS Zones to be used for this implementation.
Zones are logical groupings of TMS VLANs that have similar security needs or levels of
trust. Keep the following points in mind as you develop your design:
• It is NOT required that all VLANs be put into a TMS Zone
• A TMS VLAN can be associated with only one zone at a time
• You can create up to 19 VLAN associations
• You can configure policies that apply to all members of a zone generally, or you
can configure more granular policies that apply only to some of the members of a
zone. For example, if TMS VLANs 20 and 30 are associated with the same zone,










