TMS zl Module Planning and Implementation Guide 2009-08
Table Of Contents
- Contents
- Glossary of Acronyms and Abbreviations
- 1.0 Purpose
- 2.0 Intended Audience
- 3.0 Objectives
- 4.0 Prerequisites
- 5.0 Skills
- 6.0 The HP ProCurve Threat Management Services zl Module
- 7.0 Common TMS Security Control Points
- 8.0 Deployment Considerations
- 9.0 Installation and Preparation of the TMS zl Module
- 10.0 Configuration of the TMS zl Module
- 11.0 Using multiple HP ProCurve Threat Management Services zl Modules
- Appendix A – Additional References
- Appendix B – Sample Company Information Assets Spreadsheet
- Sample “Information Assets” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Server Network Details” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “TMS Zones” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Firewall Rules” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- /Sample “Company Information Assets” Microsoft Excel 2003 spreadsheet
- Appendix C – Information Gathering Tools
- Appendix D - Updating Switch Software
- Appendix E – Emergency Recovery Process
Page 42
you can create separate access policies for controlling the traffic to and from each
VLAN.
• If you plan to create many different policies for different TMS VLANs, it might
be easier to associate the VLANs with different zones. For example, you could
associate VLANs in your private network with three separate zones: Zone1
contains the server VLAN 10; Zone2 contains user VLAN 20, which is for regular
employees; and Zone3 contains user VLAN 30, which is for guests.
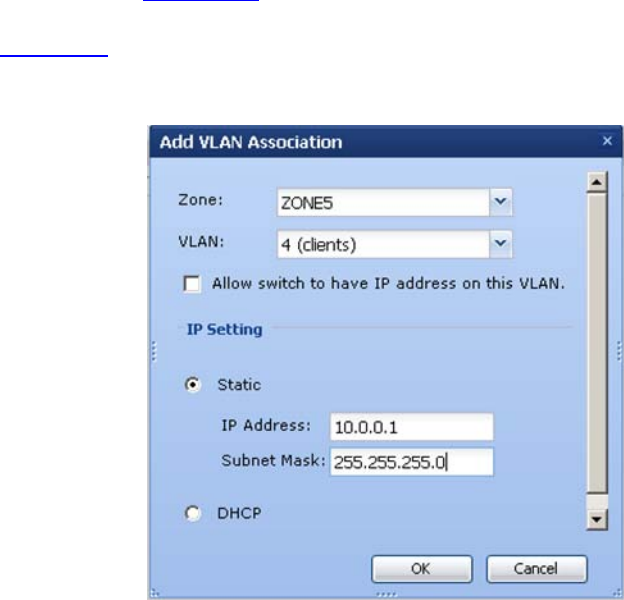
As seen in the following image, TMS Zone configuration requires identification of which
VLANs will be assigned to the Zone and the gateway IP address and Subnet Mask. Since
we now have visibility to and an understanding of the network design specifics, we need
to assign VLANs to appropriate TMS Zones. The “Company Information Assets”
spreadsheet in Appendix B includes a tab for creating your custom TMS Zone table and
provides a sample list based on the “Compartmentalization” security design discussed in
Section 7.3 of this document. The logic is straightforward – make sure that you have
each VLAN in an appropriate TMS Zone to allow for the required management of
network traffic to and from that VLAN.
The final step before configuration of the TMS zl Module is to create a list of security
controls to be implemented. When protecting an environment using the TMS zl
Module, security controls can include firewall rules, IDS/IPS configuration requirements
and/or traffic encryption (VPN) requirements. After completing the list of network
details for each server and application, review the details with the IT staff. The
discussion should be to confirm accuracy and completeness. This is also the right
opportunity to determine the appropriate user groups, level of access and any access
timeframes required for each listed application. Any need for encryption (VPN) and/or
IDS/IPS protection should also be identified.










