TMS zl Module Planning and Implementation Guide 2009-08
Table Of Contents
- Contents
- Glossary of Acronyms and Abbreviations
- 1.0 Purpose
- 2.0 Intended Audience
- 3.0 Objectives
- 4.0 Prerequisites
- 5.0 Skills
- 6.0 The HP ProCurve Threat Management Services zl Module
- 7.0 Common TMS Security Control Points
- 8.0 Deployment Considerations
- 9.0 Installation and Preparation of the TMS zl Module
- 10.0 Configuration of the TMS zl Module
- 11.0 Using multiple HP ProCurve Threat Management Services zl Modules
- Appendix A – Additional References
- Appendix B – Sample Company Information Assets Spreadsheet
- Sample “Information Assets” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Server Network Details” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “TMS Zones” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Firewall Rules” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- /Sample “Company Information Assets” Microsoft Excel 2003 spreadsheet
- Appendix C – Information Gathering Tools
- Appendix D - Updating Switch Software
- Appendix E – Emergency Recovery Process
Page 61
10.0 Configuration of the TMS zl Module
Adding a TMS zl Module to an existing environment can pose certain challenges, depending on how it
is done. In some environments, the TMS zl Module will be protecting new networks and interfacing
these networks with the rest of the network is a relatively straightforward task. In most environments,
however, we have a stable network where the TMS zl Module will be introduced to enhance the security
of the network.
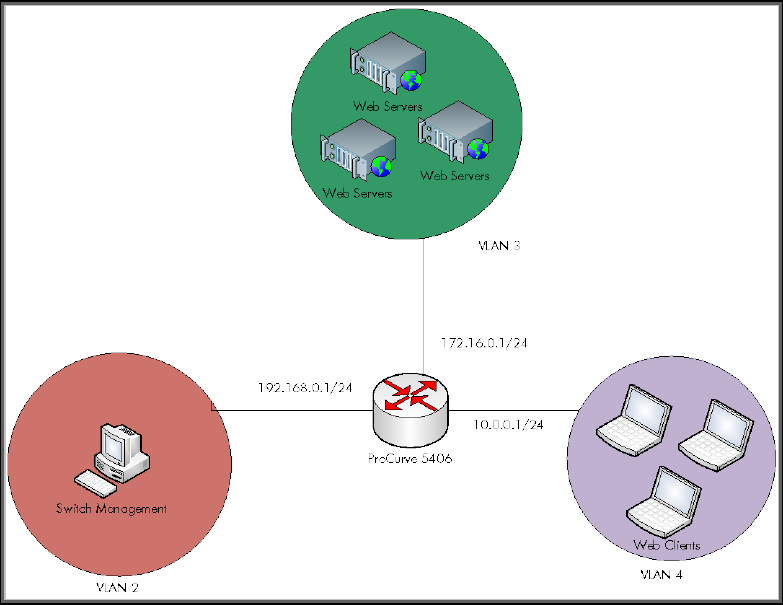
10.1 Network Diagrams
Let’s familiarize ourselves with the existing sample network first.
In this sample network, we have three main VLANs, one dedicated to switch
management, one dedicated to web servers, and one dedicated to web clients. The 5406zl
is acting as an IP router and is using extended Access Controls Lists (ACLs) to control
access from one VLAN to the other. The management VLAN is also defined and due to
its very nature, the 5406zl puts security restrictions on the management VLAN.
Figure 16