TMS zl Module Planning and Implementation Guide 2009-08
Table Of Contents
- Contents
- Glossary of Acronyms and Abbreviations
- 1.0 Purpose
- 2.0 Intended Audience
- 3.0 Objectives
- 4.0 Prerequisites
- 5.0 Skills
- 6.0 The HP ProCurve Threat Management Services zl Module
- 7.0 Common TMS Security Control Points
- 8.0 Deployment Considerations
- 9.0 Installation and Preparation of the TMS zl Module
- 10.0 Configuration of the TMS zl Module
- 11.0 Using multiple HP ProCurve Threat Management Services zl Modules
- Appendix A – Additional References
- Appendix B – Sample Company Information Assets Spreadsheet
- Sample “Information Assets” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Server Network Details” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “TMS Zones” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Firewall Rules” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- /Sample “Company Information Assets” Microsoft Excel 2003 spreadsheet
- Appendix C – Information Gathering Tools
- Appendix D - Updating Switch Software
- Appendix E – Emergency Recovery Process
Page 66
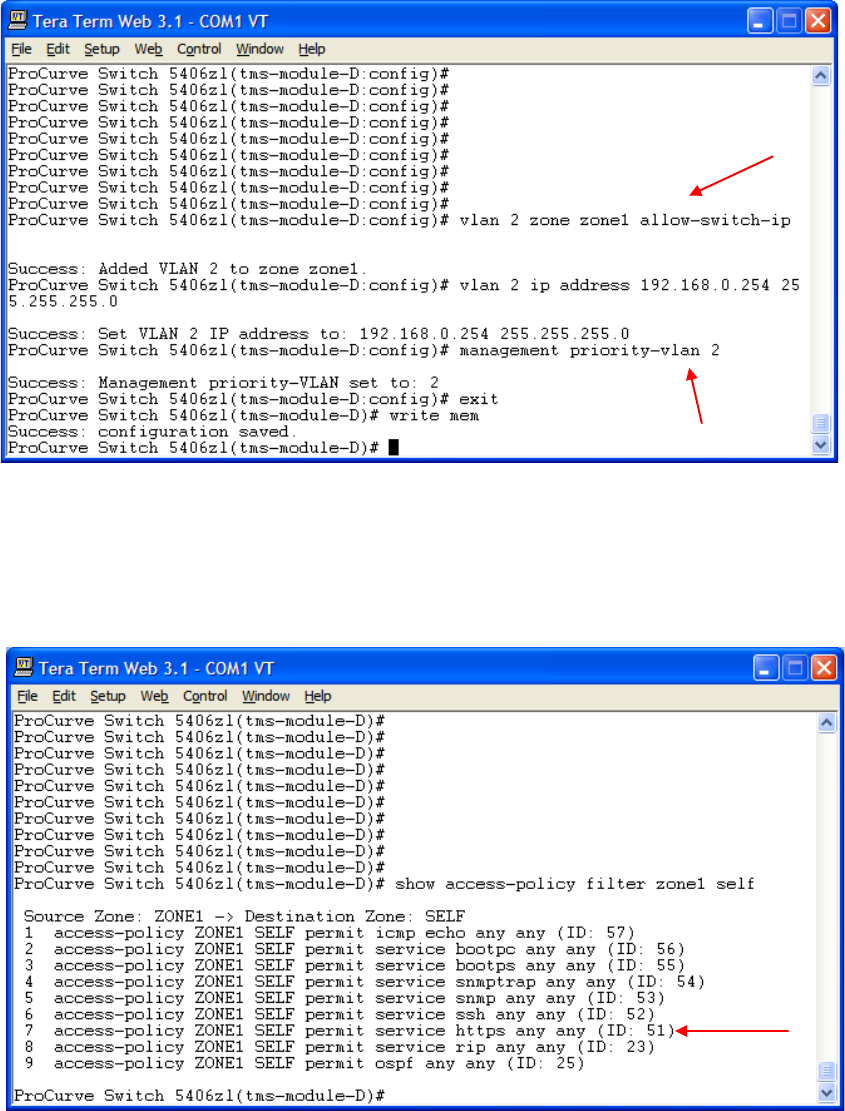
The switch management IP address is in VLAN 2. We want to add the TMS zl Module
to this VLAN as well. We want the switch chassis to keep its IP address, so we will
associate VLAN 2 with zone1, our management zone, and allow for the switch chassis to
have an IP address in the same VLAN. We then assign an IP address to the TMS zl
Module for management purposes. Then configure management priority-vlan 2 to give
any traffic on VLAN 2 management priority. Be sure to save your work with write
memory!
By identifying a management zone, we can see that the TMS zl Module has put access
policies in place that allow for management traffic between Zone1 and Self. We will be
using HTTPS to configure the TMS zl Module and we can see that HTTPS is present in
the access policy.